The landscape of mergers and acquisitions (M&A) continues to evolve, driven by factors such as advancements in artificial intelligence, digital transformation, and the need for companies to stay competitive in an ever-changing market. Despite various economic challenges, M&A activity remains robust as companies seek strategic acquisitions to expand capabilities and streamline operations.
A recent Deloitte survey of 1,500 corporate and private equity dealmakers highlights a renewed optimism in the M&A market, with many leaders adapting their strategies to navigate current uncertainties and capitalize on emerging opportunities. Additionally, sectors such as technology, energy, and industrials are poised for significant activity, with companies looking to expand their capabilities and streamline operations through strategic acquisitions.
Amid these dynamic market conditions, it is crucial for organizations to balance efficiency and security, especially in the early stages of M&A integration. Focusing on best practices for identity and access management (IAM) during M&A can help companies navigate complexities and maximize the value of their mergers and acquisitions from the outset.
What Is Identity and Access Management?
Identity and access management (IAM) refers to a framework of business policies, technologies, and processes facilitating the management of digital and electronic identities. It gives IT managers control over user access to systems and information across the organization. IAM manages the lifecycle of user identities, access, and entitlements across enterprise resources in data centers and the cloud. It has become a foundational control of cloud security since it authenticates users and regulates their access to data, systems, and networks. Some of the systems commonly used for IAM are single sign-on (SSO) systems, privileged access management, and multi-factor authentication. These technologies also enable organizations to securely store profile and identity data and allow efficient data governance. Organizations can deploy IAM systems internally, outsource to a third-party vendor through cloud-based subscription models, or via hybrid models. Organizations handling sensitive customer data, like those in the financial or healthcare sectors, can enable a zero-trust strategy.
The Need for Identity and Access Management for M&As
When organizations merge or acquire other companies, one critical item to do immediately is to determine the right levels of access to grant existing employees and what they need to complete their jobs successfully. Employees need access to multiple systems, apps, and data spanning both corporate entities. These include customer relationship management (CRM) platforms, workforce collaboration tools, human resource information systems (HRIS), accounting systems, patient care apps, banking software, and more. Unfortunately, M&A activity rapidly enables single sign-on (SSO) access to acquired employees for business continuity. While the business needs to provide access to new users, doing it too quickly creates situations where companies grant access without considering the least privileged approach.
A Core Security report on identity and access management showed that 77% of organizations have users with more access privileges than necessary. It leaves such organizations vulnerable to unauthorized access to sensitive systems, data, and applications across their network, whether intentional or not. Mergers and acquisitions come with new access and security challenges threatening normal business operations. M&A activity comes with time and operations constraints in the early days, with demands for results and shared benefits. The new organization looks to grow through acquisition and will be keen to consolidate its IT services, applications, and data to facilitate smooth operations. Improved productivity relies on a unified experience for information, systems, and network access. However, without proper planning, risks emerge, such as identity management and miscommunication arising from misalignment of terminology.
Identity Is First
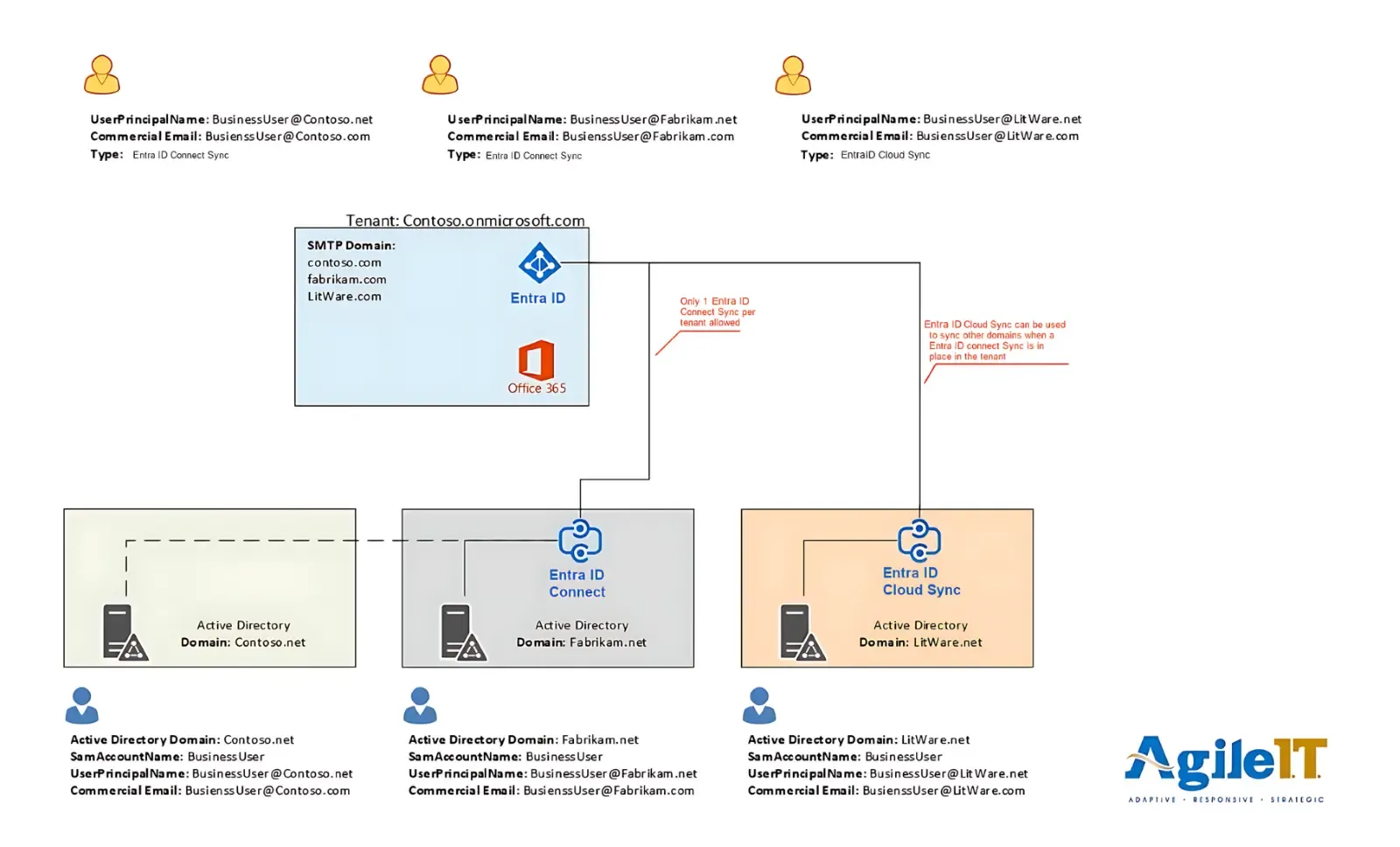
Identity always comes first because all access and services depend on identity. Organizations coming out of M&A activity must consolidate identity first before anything else. It’s a complex process considering the new size of the organization, but necessary and achievable. These complex identity consolidation scenarios require proper planning and often impact users before achieving the required result. Still, it’s less costly than a network or system breach stemming from avoidable vulnerabilities. Below is an example of an organization’s identity decisions post-M&A:
-
Entra ID and Microsoft 365
Contoso tenant becomes the future home of the consolidated cloud identities
Contoso & Fabrikam will run on Hybrid cloud-managed devices
The organization will directly join Liteware and AdventureWorks with Entra ID with Intune management
-
Local Active Directory
The organization(s) will retain local AD because of time and LOB application constraints (Fabrikam & Contoso)
It will require network connectivity between environments for other LOB, so Local AD can leverage it
The Fabrikam data center will handle Entra ID Connect between forests, syncing user, groups & devices from both the Fabrikam & Contoso Local Active directory domains.
Liteware will handle Entra ID cloud sync if there is no immediate need for hybrid device management (“Entra ID cloud sync” does not sync devices & is a lightweight sync service compared to Entra ID connect.)
-
Email and Cloud File Sharing
Contoso tenant will house all email services and the related cloud file sharing
Define the Direction
Organizations going through M&A should define the direction early on using objectives and constraints. Objectives define what the organization intends to achieve, while the constraints impact the design and assessment options. Objectives to include are:
-
Migration preparation: The organization identifies a plan for the identity project and offers guidance on what should change before it starts.
-
Security and compliance: These objectives guide leveraging systems and applications such as Microsoft services to strengthen the overall security posture.
-
LOB impacts and direction: Involves identifying and providing guidance on Line of Business (LOB) application impacts throughout the process.
The constraints include the following:
-
Dates: Is it contractual-based with deadlines?
-
Infrastructure: Networking capacities
-
Apps: They leverage a combination of Entra ID, Local AD, and AD FS
-
User access: Access to applications and systems requires users to have local AD accounts.
Assessment and Planning
The process of assessment and planning for identity access management will look like this:
- Learning and agreeing on common terminology to remove confusion and ensure everyone is on the same page
- Mapping identities, including users, groups, and devices
- Identifying naming collisions and creating explicit rules for handling them
- Collecting and understanding the licensing landscape
- Defining a clear and inclusive plan for the organization’s identity direction and execution
- Understanding how the identity plan will affect users and addressing the arising issues head-on
Key Considerations and Challenges
Below are some of the expected considerations and challenges of identity and access management:
Microsoft Licensing
- Purchasing a Microsoft Enterprise Agreement requires proper planning and consideration with the provider to ensure the timing of the license transition does not affect migrations
- Purchasing a license via Microsoft CSP with a partner requires prior planning to ensure contracts and handoff don’t affect the migrations. It comes with a different host of challenges than an enterprise agreement
Switching Primary Directories for Devices
- Devices joined to local AD or hybrid pose a significant challenge when they need to change the directory (Entra or local AD) they are enrolled in, because the user files and profiles on the device must be moved too.
- Devices enrolled directly in Entra ID or Intune also need careful planning, testing, and other manual steps to be migrated.
Prevent Significant Identity Changes During the Migration or Transition
Changing user and group attributes
Changing to the defined pattern of rules pattern required for remediation
DNS
- Timing of external changes, such as who has access and what should be changed
- Transitioning custom domains between tenants can impact email routing
Service Availability
- Understand that during a transition, there will be downtime and outages for users and devices
Documentation
- Document everything from the start and keep updating the process
- Ensure all teams understand the changes
The Demands of M&A Require Identity and Access Management
Organizations going through M&A can succeed by establishing sound identity and access management policies to ensure all users get appropriate access levels. Identity is the priority because access and services rely on it. Organizations should first consolidate identity after an M&A activity.
It’s a complex process that requires proper planning and execution since it will affect the entire organization. Organizations need to collect, aggregate, and reconcile all identities spanning across all systems immediately and make it a going concern to reduce conflicts, duplications, and last-minute headaches. The last thing a company needs is a disgruntled former employee with high-level access gaining unauthorized access to sensitive data.
Next, organizations should prevent or limit changes in the identity landscape as they execute the plan based on what they assessed and defined. Before undertaking any identity planning or definition, they must start a conversation with all the relevant licensing vendors. Automation is key to a successful, consistent, and frequent assessment and validation process. Adapting a solid IAM approach helps bolster overall organizational risk management and achieve the ideal balance between user efficiency and organizational security.
Agile IT Can Help with Identity and Access Management for M&As
When you acquire or merge with another company, you acquire or combine its assets, including different types of hardware, software licenses, and contracts. M&A activity should bring in benefits, not financial losses. Prioritize identity and access management after an M&A to ensure smooth sailing and business continuity. At Agile IT, we’ve provided different-sized companies with Microsoft Licensing and can help with IAM policies and strategies to make your M&A a success. Schedule a consultation today.
Published on: .