For organizations that work within the United States Defense Industrial Base, there is a wide array of compliance requirements needed depending on the given department, agency, and type of data and communication you are working with.
Below, we provide a brief overview of key terms and their origins, which is crucial for understanding how they will align with your requirements, ensuring you can implement the necessary security controls to adhere to federal government regulations for DoD contractors. If you know this already, navigate down to the Government Compliance Matrix to quickly dive deeper into what you’re looking for.
Leveraging Microsoft 365 GCC High and Azure Government to reduce the risk and overhead in achieving security and compliance requirements along with the productivity and innovation gains is a core motivator for many organizations.
Where does GCC come from?
The term Community Cloud originated from the National Institute of Standards and Technology (NIST) Special Publication 800-145, “The NIST Definition of Cloud Computing” (https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf) Microsoft, therefore, has created Government Community Cloud (GCC) and Government Community Cloud High (GCCH) as separate cloud instances with distinct controls and requirements.
The following is a snippet from that publication:Private cloud
The cloud infrastructure is provisioned for exclusive use by a single organization comprising multiple consumers (e.g., business units). It may be owned, managed, and operated by the organization, a third party, or some combination, and it may exist on or off premises.
Community cloud
The cloud infrastructure is provisioned for exclusive use by a specific community of consumers from organizations that have shared concerns (e.g., mission, security requirements, policy, and compliance considerations). It may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination, and it may exist on or off premises.
Public cloud
The cloud infrastructure is provisioned for open use by the general public. It may be owned, managed, and operated by a business, academic, or government organization, or some combination. It exists on the premises of the cloud provider.
Hybrid cloud
The cloud infrastructure is a composition of two or more distinct cloud infrastructures (private, community, or public) that remain unique entities, but are bound together by standardized or proprietary technology that enables data and application portability (e.g., cloud bursting for load balancing between clouds).
What’s the difference between GCC and GCC High?
The Government attachment to the phrase “Community Cloud” and the distinguishment of Low, Moderate and High also come from NIST and leveraged by FedRAMP.
The following snippet is from FedRAMP: https://www.fedramp.gov/baselines/
Federal Information Processing Standard (FIPS) 199 provides the standards for the security categorization of federal information and information systems. FedRAMP authorizes Cloud Service Offerings (CSOs) at the: Low (including Tailored Li-SaaS), Moderate, and High impact levels. FedRAMP Tailored was developed to support industry solutions that are low risk and low cost for agencies to deploy and use. Tailored policy and requirements provide a more efficient path for Low Impact-Software as a Service (LI-SaaS) providers. The LI-SaaS Baseline accounts for Low-Impact SaaS applications that do not store personal identifiable information (PII) beyond that is generally required for login capability (i.e. username, password, and email address).
Now we can put all this together and we get:
- Office 365 Multi-Tenant, FedRAMP Moderate, Authorized but does NOT meet other requirements for CMMC Compliance.
- Government Community Cloud (GCC), FedRAMP Moderate Authorized but does not meet other requirements for CMMC L2 compliance.
- Government Community Cloud High (GCC High), FedRAMP High Equivalence, and is the desired cloud instance for OSAs.1.
Buyer Beware
There are new offerings showing up on the Internet that say you don’t need GCC or GCC High and claim to meet government requirements.
We recommend the following:
- Visit the FedRAMP Marketplace to see if they’re approved at the level you require.
- Validate with an assessment/auditor
What is Microsoft GCC and GCC High
- GCC is Office 365 paired with Microsoft Entra ID in Azure (Commercial). It is intended for contractors holding or processing data on behalf of the US Government that is not CUI or ITAR data.
- GCC High is Office 365 paired with Microsoft Entra ID in Azure (Government). It is intended for contractors storing, processing, or transmitting Controlled Unclassified Information (CUI) or subject to International Traffic in Arms Regulations (ITAR) on behalf of the United States Department of Defense.
As defined by Microsoft: https://learn.microsoft.com/en-us/office365/servicedescriptions/office-365-platform-service-description/office-365-us-government/office-365-us-government#about-office-365-government-environments
GCC
The Office 365 GCC environment provides compliance with federal requirements for cloud services, including FedRAMP High, Defense Federal Acquisition Regulations Supplement (DFARS), and requirements for criminal justice and federal tax information systems (CJI and FTI data types).
GCC High
The Office 365 GCC High and DoD environments deliver compliance with Department of Defense Security Requirements Guidelines, Defense Federal Acquisition Regulations Supplement (DFARS), and International Traffic in Arms Regulations (ITAR).
GCC High isn’t just a marketing name and small differences in licensing and deployment. It’s way more than that.
Cybersecurity Maturity Model Certification (CMMC)
For those companies that do business with the DoD, it is even more crucial that sensitive data is kept out of the hands of bad actors. These companies include all suppliers, commercial item contractors as well as subcontractors to larger companies that work within the Defense Industrial Base sector. To address this issue, the DoD launched the Cybersecurity Maturity Model Certification (CMMC) program. Currently in version 2.0, this iteration streamlines requirements to three levels of cybersecurity and aligns the requirements at each level with well-known and widely accepted NIST cybersecurity standards. Prior to this certification requirement, companies were not subject to external audits to verify stringent data security measures. GCC High helps ensure you are on your path to compliancy.
International Traffic in Arms Regulations (ITAR)
Navigating regulatory landscapes is a crucial aspect of digital transformation. With expertise in ITAR regulations, Agile IT ensures your Microsoft 365 GCC High tenant aligns with these stringent requirements. By leveraging Microsoft’s GCC High’s ITAR-compliant environment, we enable your organization to handle defense-related articles and services with unwavering confidence in data security and regulatory compliance.
In a cloud setting, technical data related to defense articles and services is going to be the primary driver of compliance. Securing ITAR-controlled data is a crucial step towards avoiding ITAR fines. While the fines themselves can be harsh, actions can also result in the loss of contracts or relationships with federal entities — as well as civil or criminal actions. Civil fines can cost you +$1 million per infraction.
“ITAR violations can have other consequences as well, including the denial/revocation of licenses and other export authorizations, compliance oversight, and the loss of business opportunities.” By Directorate of Defense Trade Controls (DDTC) – U.S. Department of State
We always recommend working with an assessment/auditing organization. Agile IT is here to help!
Learn more about the Microsoft GCC and GCC High offerings to align to your requirements.
You’ve decided to move to a Microsoft 365 using either Government Community Cloud Moderate (GCC) or Government Community Cloud High (GCC High) to meet your Public Sector compliance requirements.
The next step is to get validated and understand licensing.
Below, we focus on key areas of planning and validation, whether you’re handing this independently, with another provider, or with Agile IT (our recommended choice 😊 ).
Licensing
Understanding the licensing options and process for either GCC is a critical part of an organization’s planning.
Microsoft 365 GCC
Licensing for GCC (aka GCC Moderate) is straight forward as it aligns with Microsoft 365 commercial (aka Global) infrastructure. However, it still requires you to get validated (the section lower on this page) and ensure you’re working with a Microsoft partner that is also approved to resell those licenses to customers (such as Agile IT).
The good news is product and feature availability, and the method of licensing and billing are virtually the same as commercial. While pricing can be slightly different in some areas, those difference are rare.
The Microsoft “Cloud Service Provider” program is intended to allow Microsoft partners to resell Microsoft licensing, but with some commitments to guidance, billing, and licensing support.
There are two types of CSP partners: Direct and Indirect.
- Direct is a partner that is invoiced from Microsoft directly for the licenses and consumption of their customers. (Agile IT is a Direct CSP partner)
- Indirect is a partner that utilizes a third-party service that offloads the Microsoft relationship and may even include added services including a requirement to pay for support.
Buyer Beware
Microsoft CSP Indirect partners add another organization and their employees into the sphere of concern regarding access, background checks, etc.
We recommend the following:
- Ask your licensing provider if they are a Direct or Indirect partner
- If you decide to work with an Indirect CSP Partner, make sure to validate which organization(s) have access to your Microsoft tenant, what that level of access is, and that logging has been configured to tract/monitor that access.
Microsoft 365 GCC High
Licensing with GCC High is unique in many ways and often misunderstood.
The Microsoft Agreement for Online Services, Government (AOS-G) is the only way for organizations to purchase Microsoft 365 GCC High licensing without the requirement of purchasing a Microsoft Enterprise Agreement.
What you should know about licensing Microsoft 365 GCC High:
- Annual and Triennial Agreements
- Pricing is defined per month to allow for mid-term additions, but licenses are paid for and provisioned on an annual basis, with triennial agreements allowing for annual true-ups and annual payment.
- You can add additional licenses throughout your term on a prorated basis.
- Licensing Increase
- Yes, it’s more expensive (payment is collected annually instead of the “as you go” contract with commercial/gcc)
- How much more expensive depends on the license, the pricing CAN change each month (this doesn’t happen often).
- Availability
- Not all Microsoft 365, Defender, or Power Platform licensing options are on the GCCH price list and your licensing provider should be able to inform you accurately.
- License Names
Microsoft documentation will refer to products in GCC High with different naming patterns
- Example: Microsoft 365 G3 is for GCC High and its equivalent is Microsoft 365 E3.
The licensing you purchase might show up different in the portal
- After you purchase your license (e.g. Microsoft 365 G3) and activate in your GCC High tenant, the list of product names may look different than what you purchased.
- The difference in names in the portal versus your invoice can be confusing but doesn’t mean something is wrong.
- Example: Microsoft 365 G3 is for GCC High and its equivalent is Microsoft 365 E3.
- Azure Government
- Azure Government is on the GCC High price list. However, Azure Government subscriptions are available to purchase via AOS-G or via Cloud Solution Provider (CSP).
Agile IT recommends purchasing via CSP as it can be more flexible and allows you greater control over the resources that you choose to provision within Azure Government.
- Azure Government is on the GCC High price list. However, Azure Government subscriptions are available to purchase via AOS-G or via Cloud Solution Provider (CSP).
Azure Government should ALWAYS be purchased. This is covered in Step 3: Government Onboarding & Migration.
Validation
- Getting access to a Microsoft 365 GCC or GCC High tenant requires validation from Microsoft directly via the Government Community Cloud Eligibility Intake Form.
Category
- This page in the form will focus on what kind of tenant you’re requesting and an option to just get validated and/or provision a trial/production tenant (See our recommendation before selecting).
Select a category
- Your selection here will determine if you’re submitting for GCC or GCC High.
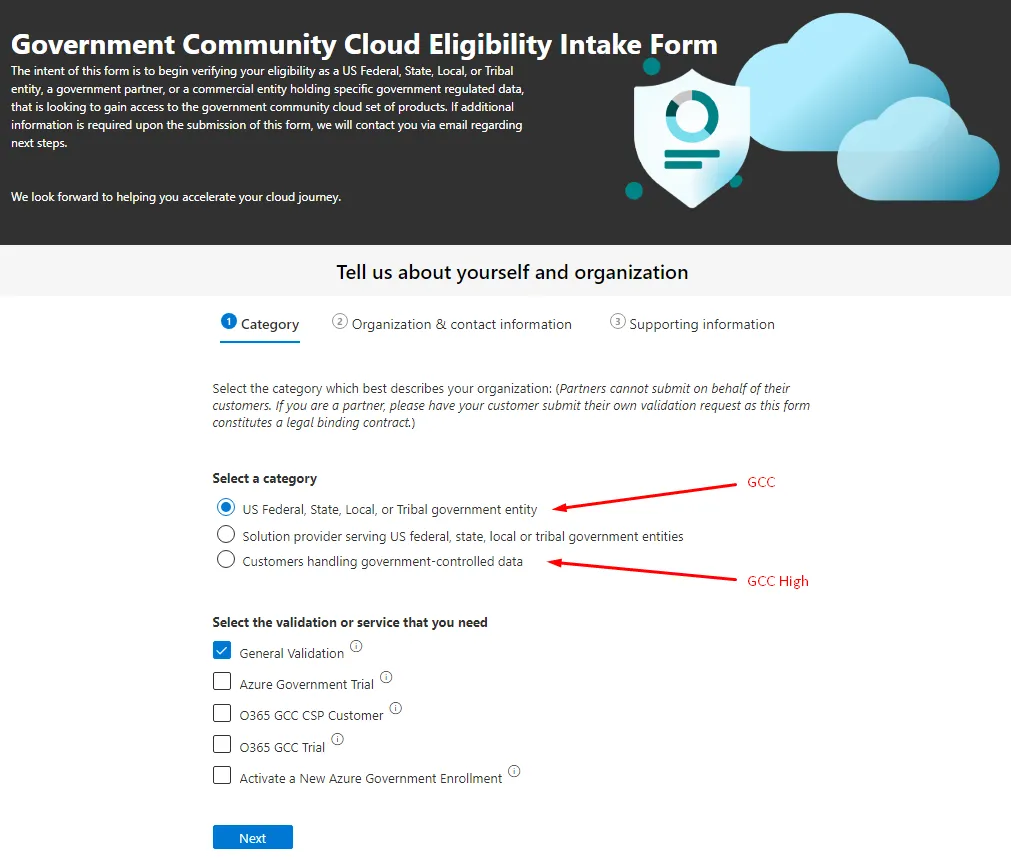
US Federal, State, Local, or Tribal government entity
- This option is for GCC
Solution provider serving US federal, state, local or tribal government entities
-
This option is for Microsoft partners. This is used when a Microsoft partner is looking to qualify for programs that require Government validation
-
As an example, Agile IT completed this many years ago to provide Azure Government and Microsoft 365 GCC and GCC High reseller licensing
Customers handling government-controlled data
- This option is for GCC High
Depending on your category selection on page 1 of the Intake Form, the options you are shown on Page 3: Supporting Information will be different.
Select the validation or service that you need
If you’re just “trying things out” or plan to do this all on your own (hopefully you’ve done this before), then you’re welcome to use any of the available options.
Recommendation:
Select, “General Validation” as this is really the most important step. This also prevents issues that can occur if you plan to use a Microsoft Partner, like Agile IT or with your existing Microsoft Large Service Provider (LSP), formerly known as a Large Account Reseller (LAR), in regards to licensing, tenant naming, activation, etc.
-
General Validation
-
This is used solely to validate customer eligibility to purchase/use the Microsoft Government Cloud.
-
This will not trigger tenant creation in Azure Government.
-
-
Azure Government Trial
- This will validate eligibility and provide a free 90-day trial of Azure Government if validation eligibility is approved. This will trigger tenant creation in Azure Government. You will be asked to input a credit card upon validation, as your Azure Government subscription will automatically convert to a Pay-As-You-Go (PAYG) subscription after 90 days.
-
O365 GCC CSP Customer
-
This will validate eligibility and tie the organization being validated to their Direct Partner’s tenant ID if validation eligibility is approved.
-
All company and contact information must be the client organization being validated, but the tenant ID provided must be the Direct Partner tenant ID.
-
Directions for your partner to find their correct Direct Partner tenant ID can be found here: O365 GCC CSP Step-by-Step Guide.
-
-
O356 GCC Trial
-
This will validate eligibility and provide a free 30-day, 25-user O365 GCC Trial code if validation eligibility is approved.
-
Note: this is an O365 GCC trial only. Microsoft does not offer GCC High trials, but an approved organization may purchase O365 GCC High if validated and approved as eligible. Entities only seeking to purchase GCC High should select General Validation above.
-
-
Activate a New Azure Government Enrollment
-
All information submitted, including the organization and contact info as well as the enterprise agreement number, must be for the same organization seeking eligibility.
-
This will trigger tenant creation in Azure Government.
-
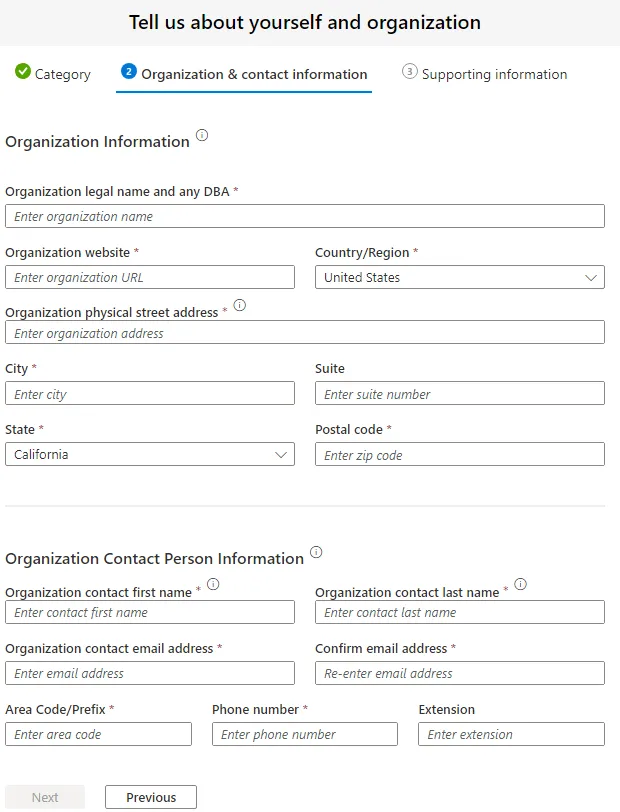
Organization & contact information
This page in the form will collect organizational and contact information.
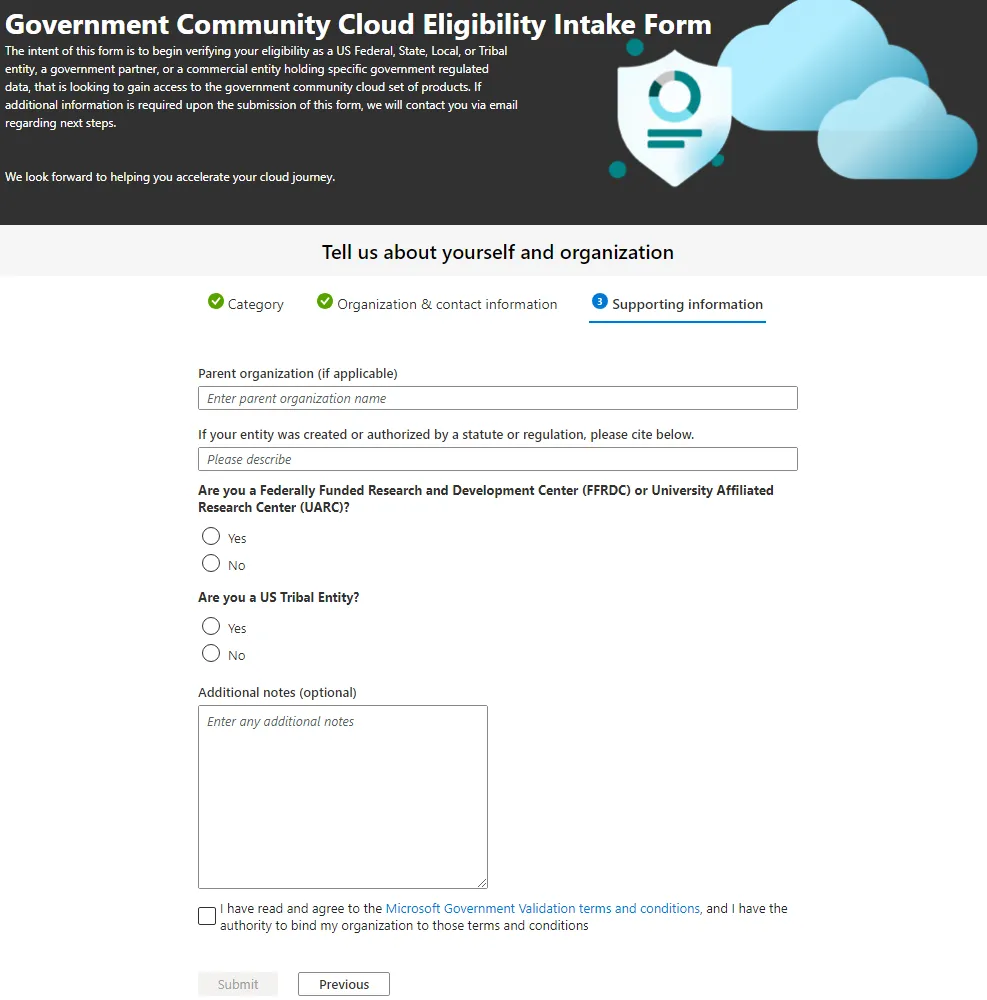
Supporting Information (GCC)
When “US Federal, State, Local, or Tribal government entity” was selected (this is for GCC). You will only need to answer a few items listed below:
- Parent organization (if applicable): Enter parent organization name
- If your entity was created or authorized by a statute or regulation, please cite below.: Please describe
- Are you a Federally Funded Research and Development Center (FFRDC) or University
- Affiliated Research Center (UARC)? (Yes or No)
- Are you a US Tribal Entity? (Yes or No)
- Additional notes (optional):
Supporting Information (GCC High)
When “Customers handling government-controlled data” was selected (this is for GCC High). You will need to enter in your CAGE number, confirm your registration with any of the listed government agencies, and select whether or not you are registered with any Small Business Association.
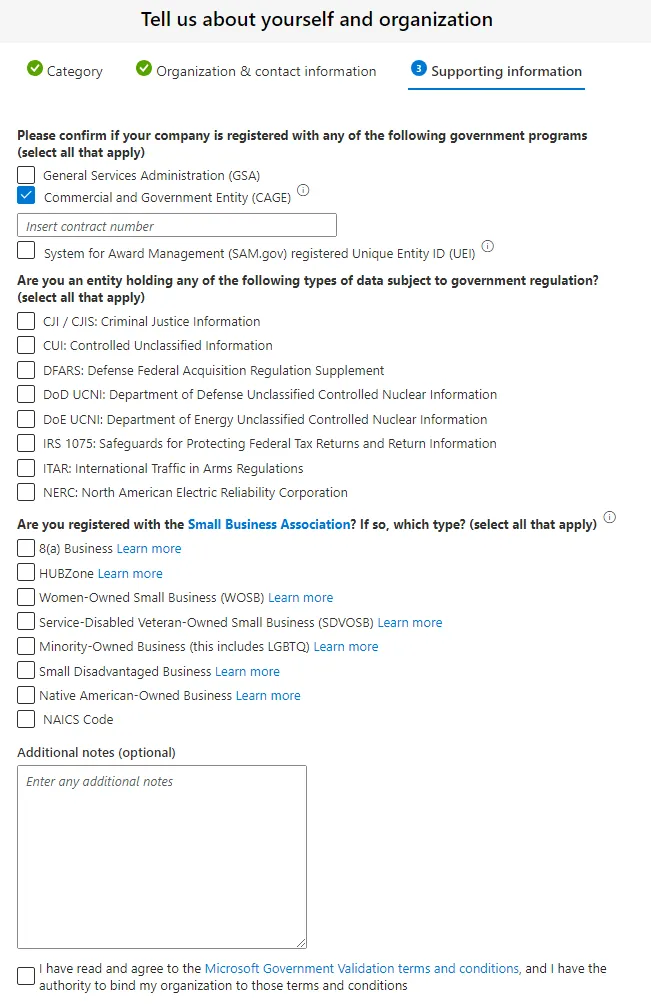
Please confirm if your company is registered with any of the following government programs
For each item you select, you will be required to insert the “contract number”
-
General Services Administration (GSA)
-
Commercial and Government Entity (CAGE)
This must be a valid CAGE code for your company and must have a status of “Active”
-
System for Award Management (SAM.gov) registered Unique Entity ID (UEI)
This must be a valid SAM.gov registered UEI with the Registration Status as “Active Registration” and the Purpose of Registration as “All Awards”.
Are you an entity holding any of the following types of data subject to government regulation?
-
CJI / CJIS: Criminal Justice Information
-
CUI: Controlled Unclassified Information
-
DFARS: Defense Federal Acquisition Regulation Supplement
-
DoD UCNI: Department of Defense Unclassified Controlled Nuclear Information
-
DoE UCNI: Department of Energy Unclassified Controlled Nuclear Information
-
IRS 1075: Safeguards for Protecting Federal Tax Returns and Return Information
-
ITAR: International Traffic in Arms Regulations
-
NERC: North American Electric Reliability Corporation
Are you registered with the Small Business Association?
The government tries to award a certain percentage of all federal prime contracting dollars to small businesses that meet certain socio-economic conditions.
The SBA provides several programs to help small businesses win federal contracts.
-
8(a) Business Learn More
-
HubZone Learn More
-
Women-Owned Small Business (WOSB) Learn More
-
Service-Disabled Veteran-Owned Small Business (SDVOSB) Learn More
-
Minority-Owned Business (this includes LGBTQ) Learn More
-
Small Disadvantaged Business Learn More
-
Native American-Owned Business Learn More
-
NAICS Code
”Separate by commas if you have multiple codes”
Eligibility Intake Form
Now you’re ready to submit for Government validation with Microsoft!
With an understanding of the compliance requirements and Microsoft validation and licensing, it’s now time to focus on securing the environment and migrating your users and data.
As Microsoft states that GCC High is required for CMMC L2, this page focuses on adopting GCC High. For organizations with less stringent requirements, see our page on migrating GCC (A Guide to Migrating to Microsoft 365 Government Community Cloud (GCC and GCC High) Agile IT).
Don’t know which environment is for you? We can help! (Microsoft 365 Security & Compliance experts in GCC High & CMMC ecosystem).
Here, we focus on key areas to consider, address, and make decisions about the scope of migration, deployment of security services, and documentation on how you are meeting the controls within CMMC.
Key Considerations
Migrating and deploying a new environment with Microsoft 365 Government Community Cloud (GCC) High and Azure Government requires careful planning and consideration.
Here are some key considerations:
1. Licensing Costs
GCC High licensing is more expensive than Commercial licensing. Read more about the differences.
2. Compliance Requirements
Are you beholden to CMMC L2, or do your contracts only call for CMMC L1? If L1, you may be over-committing by migrating to GCC High, and GCC might be a better solution.
3. Data Residency and Sovereignty
Not all FCI has the same requirements. For a better understanding of CUI, download our whitepaper.
4. Identity and Access Management
CMMC imposes strict access controls, Microsoft GCC High can take much of the technical implementation burden.
5. Security and Monitoring
Many MSP’s will want to sell you additional MSP-friendly tools and agents for security and monitoring. Your Microsoft 365 GCC High licenses may already include many of these capabilities, don’t overpay for similar services.
6. Interoperability and Integration
GCC High has similar but not full feature parity with Commercial. Enabling things like Cross-Tenant Collaboration and SSO helps keep you employees productive and secure.
7. Backup and Disaster Recovery
There are many backup solutions available, but not all have FedRAMP authorization or equivalency. Read more about Agile IT’s solution.
8. Continuous Review and Updates
CMMC requires continuous compliance to maintain contracts within the DIB. AgileDefend offsets the internal effort required to maintain compliance. Learn more about AgileDefend.
Agile IT Services for GCC High Onboarding & Migrations
At Agile IT, we’re not just proficient in addressing the complexities of government regulations and compliance standards while ensuring top-tier security measures – we excel at them, demonstrated by our Microsoft Partner of the Year award in Security and Compliance.
Our focus? Providing secure, compliant cloud solutions with Azure Government and Microsoft 365 GCC High. Designed to fit the distinctive needs of defense, federal, state, and local government organizations.
Migrations to Microsoft 365 GCC and GCC High
Our migrations to Microsoft 365 take a unique focus and process due to the technical, security, and compliance requirements that are critical to customer success.Learn MoreModern Desktop
Agile IT’s Modern Desktop solution is ideal for customer transitioning to Microsoft 365 GCC High.Learn MoreModern Endpoint Management
Agile IT’s Modern Endpoint solution leverages customer’s GCC High environment with Microsoft Intune to meet security, management, and compliance requirements. This is also key for vendor consolidation, cost management, and reducing costs in IT training and support.Learn MoreWhen a government subcontractor is seeking a Managed Service Provider (MSP) for Microsoft 365 Government Community Cloud (GCC) High to ensure compliance with CMMC (Cybersecurity Maturity Model Certification), there are specific criteria and considerations to keep in mind. The GCC High environment is designed to meet the stringent compliance requirements of the U.S. Department of Defense (DoD) and other federal agencies, so it’s essential to choose an MSP that understands and can navigate this unique environment.
Here are some key considerations and criteria to look for in ANY MSP:
1. Compliance and Certifications:
CMMC: MSPs are not required to be directly certified in CMMC. However, if they provide services within the scope of a CMMC assessment, your MSP will need to be included in your audit as an MSP’s environment, controls, and procedures must align with the appropriate CMMC level requirements you are targeting. Working with an MSP that is already CMMC certified provides several advantages such as streamlined compliance process, reduced risk, faster path to certification, and a true alignment with federal security standards.
NIST SP 800-171: MSPs must comply with the security requirements outlined in NIST Special Publication 800-171 R2, which provides guidelines on protecting CUI. Although NIST SP 800-171 R3 has been published, R2 version is codified in the Final Rule of CFR Title 32: Cybersecurity Maturity Model Certification Program. This compliance is foundational for CMMC and is necessary to achieve CMMC Level 2 and beyond.
Federal Risk and Authorization Management Program (FedRAMP): For CMMC, MSPs must use FedRAMP-authorized or compliant cloud service providers to handle CUI, typically requiring FedRAMP Moderate or High authorization or equivalency.
2. Experience with GCC High:
The MSP should have a proven track record of deploying, managing, and supporting Microsoft 365 GCC High environments.3. Security Expertise:
Given the sensitive nature of the data, the MSP should have a strong focus on security, including:- Regular security audits and assessments
- Proactive monitoring for threats and vulnerabilities.
- Incident response capabilities.
4. Data Sovereignty:
Ensure the MSP understands the importance of data sovereignty and can guarantee that data remains within the U.S., as required by GCC High. This includes ensuring that all support is performed by United States Citizens, who are working within United States.5. Migration Expertise:
If you’re transitioning from another environment, the MSP should have experience in migrating data and applications to GCC High without data loss or downtime.6. Training and Support:
The MSP should offer training for your staff on the GCC High environment and provide robust support, including a dedicated account manager or support team familiar with your setup.7. Service Level Agreements (SLAs):
Ensure the MSP offers SLAs that match your organization’s needs, especially in terms of uptime, response times, and resolution times.8. Customization and Integration:
The MSP should be capable of customizing the GCC High environment to suit your needs and integrate with other tools or systems you use.9. Backup and Disaster Recovery:
Ensure the MSP offers robust backup and disaster recovery solutions, especially given the critical nature of government data.10. Transparent Pricing:
The MSP should provide clear and transparent pricing, with no hidden fees. They should also be willing to discuss and negotiate terms that suit your organization’s budget and compliance goals.11. Continuous Monitoring and Reporting:
The MSP should offer continuous monitoring of your environment and provide regular reports on performance, security, and compliance.12. Innovation and Future-Proofing:
As technology and compliance requirements evolve, the MSP should demonstrate a commitment to staying updated and ensuring your environment remains compliant and efficient.In conclusion, when selecting an MSP for Microsoft 365 GCC High, it’s imperative to prioritize compliance, security, and experience. Given the unique requirements of the GCC High environment, partnering with an MSP that understands and can navigate these complexities will be invaluable. Agile IT is here to help!
Read more about our MSP service, AgileDefend, here.
