
Internet of Things (IoT) in the Workplace (Video)
Explore the transformative role of IoT in modern workplaces. Watch our video to understand the impact and benefits of IoT integration
Explore related topics in this category

Explore the transformative role of IoT in modern workplaces. Watch our video to understand the impact and benefits of IoT integration
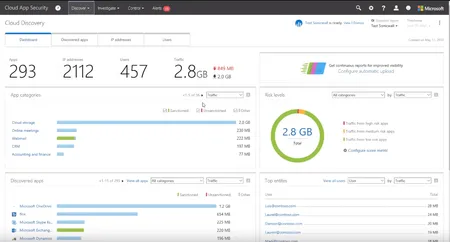
Learn how to tackle shadow IT using EMS and Cloud App Security in Agile IT's video, offering insights into identifying and managing unauthorized IT practices.
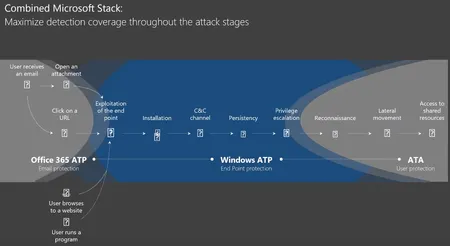
Uncover key strategies to defend against ransomware and rapid cyberattacks with Agile IT's video, highlighting Microsoft's advanced security solutions.

As we addressed a previous post, Microsoft Office 365 is a secure cloud-based platform for information and document management, providing a comprehensive overview of Microsoft cloud services...

The relationship between Microsoft Teams and SharePoint and which to use for specific purposes is a common point of confusion for our new customers...

Jerry Stidham is a Cloud Deployment Specialist and all around Microsoft guru for us here at Agile IT He has recently taken the time out from helpin...

Cloud software is taking over everywhere with lots of good reasons Software publishers are looking into shifting their business model Some want to...

UPDATE On May 24th the FBI announced that they had removed Photobucket images that were used to hide VPNFilter command and control IP addresse...

The FBI now calls ransomwarenewsransomwareprotectionoffice365 attacks a stylefontweight 400billion dollar a year crimestyle...

Today every business knows that a migration to the cloud is necessary The productivity gains of going paperless and the sheer speed of a digitally...