Combating Shadow IT with EMS and Cloud App Security (VIDEO)
Uncover key strategies to defend against ransomware and rapid cyberattacks with Agile IT's video, highlighting Microsoft's advanced security solutions.
Tech Talks are a weekly opportunity to learn how to do more with your cloud software and services. Each week, we feature a short talk from a subject matter expert, followed by a community driven Q&A where Agile IT customers can ask engineers any of their most pressing questions. This is a free service for our managed service clients. June 21st’s Tech Talk featured a discussion on Identifying Shadow IT using EMS and Cloud App Security by Kevin Martins, a Microsoft security expert.
Navigating and identifying Shadow IT threats in EMS and Cloud App Security
When we talk about Shadow IT, what happens commonly is that you have a new employee, in this case the head of HR. At their last company, they were using some sort of cloud collaboration app, and when they start with your company, they also start using it with their team. Soon you discover that you have a group of 5-10 people using an un-vetted app to get work done faster, which is great in itself, but what information is going there?
- Is there personally identifiable information (PII)?
- Are they communicating social security numbers, or other protected data?
- Does the service comply with the data compliance rules your company must follow, be it HIPPA, PCI or GDPR?
- Where is the data going?
- Where is hosted
- Is it encrypted?
Now you have a Shadow IT problem
Using your firewall logs to identify Shadow IT
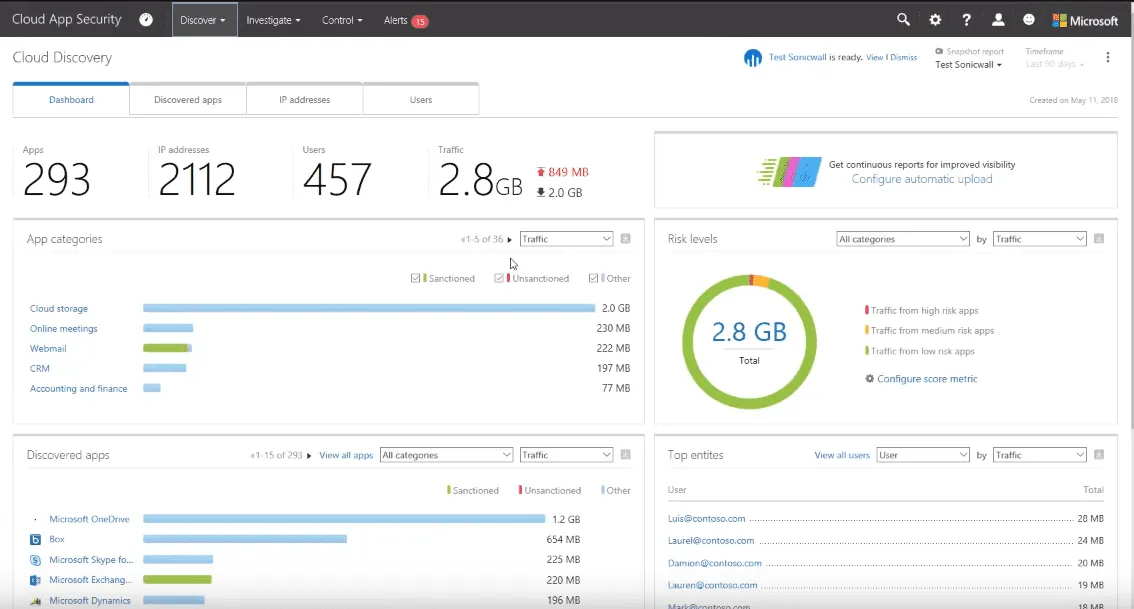
 Cloud App Security (CAS) can import system logs from over 20 different flavors of Firewalls, including Sonicwall, Sysco, Palo Alto Networks, Watch Guard and many more. There is also a custom log format tool in the application that allows you to set up CAS for any logs you may have. For the purpose of this demo, the data came from a fictitious Sonicwall environment used for Microsoft demos and testing.
Cloud App Security (CAS) can import system logs from over 20 different flavors of Firewalls, including Sonicwall, Sysco, Palo Alto Networks, Watch Guard and many more. There is also a custom log format tool in the application that allows you to set up CAS for any logs you may have. For the purpose of this demo, the data came from a fictitious Sonicwall environment used for Microsoft demos and testing.
A day’s worth of logs for a medium to large business can be parsed in a few hours. Once this is done, there is a catalog of over 16,000 cloud applications that can be checked for and analyzed. Right away, on the dashboard, you can see how many applications, how many IP addresses, how many users, and how much bandwidth use (both upload and download) has occurred.
You also get a quick overview of your top used apps, ranked by bandwidth, and grouped by type. You can see who your top bandwidth consumers are, along with total bandwidth used. Each data point can be clicked on to drill down into the data. At the bottom of the dashboard is a locations map, that allows you to see where in the world the information is being sent. By hovering over regions, you can see how many apps are in each country. Clicking on the map lets you quickly see what apps are hosted in the country.
In this case, clicking on Russia identifies a few old installs of Kapersky that have been left behind. One click, and you get a full overview of the app including:
- Risk level
- Security Features (SAML, HTTPS, encryption protocol, Heartbleed patch status, and DROWN protection, etc)
- Compliance certifications (HIPPA, GDPR ISO 27001, SOX, SOC , FINRA, etc)
- Which of your users are using the app
Researching Shadow IT instances, including user identification
In addition to by the map, you can also pull up a list of applications in use, and filter based on the overall security score. From here, you can just click on the name to find out which users have interacted with it. This makes it very easy to identify malware, and also to track down end-users so you can investigate any suspected security incidents.
Setting alert and blocking rules for common cyber security vulnerabilities
Being able to see these things is incredibly useful, but most of us are too busy to check syslogs daily. Kevin next delves into Cloud App Security’s Policies and Templates and how to configure them to alert you to anomalous behaviors. You can create your own alerts and policies, but to get you started, there are pages of pre-defined templates that can be customized for your business, some examples are:
- Files containing Personally Identifiable Information detected in the cloud
- New cloud storage apps
- Logins from risky IP addresses
- Admin activity from a non-corporate IP address
- Potential malware activity
In the Tech Talk, Kevin walks through the setup to detect potential malware activity. In this case, it utilizes commonly known ransomware file extensions to generate an alert. The alert can be fully customized to include method (Email or SMS) , activity, frequency and severity, keeping you from getting swamped by needless warning and allowing you to focus on the biggest potential threats. Additionally, you can choose to block many activities completely.
His next example is identifying anomalous download by a single user. This kind of activity could indicate a compromised account, or the internal theft of company information. Also protecting from data loss are templates that can identify when information is shared with an unauthorized domain (a competitor), and even to identify when proprietary source code is shared or emailed.
Machine learning policies to detect anomalous user behavior
Kevin wraps up with a quick talk about how Cloud App Security uses machine learning to identify normal behaviors in your network so you can then create alerts or policies around anomalies. For the first two weeks the app is running it is actively learning how your users behave. When and where they login from, how much bandwidth they use and where are just a few of the behavioral data points that can then be used to create alerts. (Joe, who typically uploads 15mb per day, just uploaded 2 gigs).
In just 15 minutes, Kevin gives a great introduction to the robust security and monitoring available in Cloud App Security. However he has barely scratched the surface of what is available. If you already have a Microsoft 365 license, you probably also have access to this tool set. To find out more about configurations and managed security services, feel free to book a 30 minute consultation with one of our Cloud Service Advisors.





