
A Guide to Planning Zero Trust Architectures - Part 1
The days of castleandmoat cybersecurity are over At least theyshouldbe over The old model is no longer cutting itnot even close Across the...
Explore related topics in this category

The days of castleandmoat cybersecurity are over At least theyshouldbe over The old model is no longer cutting itnot even close Across the...

When youre using software especially complex suites loaded with apps its easy to slip into the path of least resistance You tend to lean on the a...

Microsoft has become the foundation of most educational institutions Communication and scheduling are handled through Outlook Documents are created ...

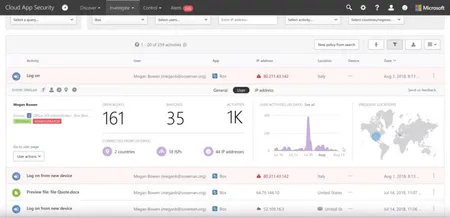
As the CEO of Agile IT Im both a special case and typical executive user of devices within the work placeThe following is a picture of my day to ...
Watch Agile IT's Azure SQL Migration demo to learn seamless database migration strategies and modernize applications with Azure cloud solutions.

Windows 10 may have been released in 2015 but its comprehensive nature evergrowing offers and numerous editions still have businesses evaluating w...

What is Microsoft TeamsAt its core MS Teams is a software platform that provides a workforce with a single space to share information and...

Get essential tips to help detect hackers and prevent breaches, ensuring your business stays protected in the face of growing cybersecurity challenges.

Stay protected online. Watch our video on the latest firewall recommendations and updates for internet and cloud security

To keep your networks secure you need to know about everything thats on them The two leading items on the Center for Internet Securitys list of ...