Protect Your Data Outside Office 365 Cloud App Security Demo
Watch Agile IT's Azure SQL Migration demo to learn seamless database migration strategies and modernize applications with Azure cloud solutions.
Tech Talks are a weekly opportunity to learn how to do more, and do it securely with your cloud software and services. Each week, we host a short talk from a subject matter expert, followed by a community driven Q&A where Agile IT’s clients can ask our engineers any of their most pressing questions. This is a free service for our clients. August 16th’s Tech Talk featured Matt Soseman, Microsoft Security Architect, who provided a helpful overview of using Cloud App Security to protect data even once it leaves your company using Microsoft’s Cloud App Security in Office 365 Enterprise.
Shadow IT and SaaS Adoption?
According to the Cloud Security Alliance, Although 73% of enterprises said that security concerns and challenges were preventing them from moving completely to the cloud, 80% of employees reported using non-approved SaaS apps in their worplace. Ironically, the concern for security is causing reduced security, as unapproved and un-monitored applications create vulnerabilities.
How Data Management Has Changed
Until recently, almost all business data was stored on company servers, workstations and devices and managed by the IT department. Today, thanks to Bring Your Own Device (BYOD) policies, not only do employees use thir own mobile devices, they also bring their own cloud. It may be easier for them to use DropBox, Slack, or Google Drive than it is to use sanctioned solutions. This makes it incredibly difficult to remain secure, but also to remain compliant with regulatory requirements like HIPPA, GDPR, etc.
Using Azure Active Directory to Bring Everything Under One Umbrella
Using Azure Active Directory (AD) to create a single sign on (SSO) identity that logs a user into all their applications with a single set of secure credentials not only makes onboarding fast, it also allows you to shut down access to everything if suspicious activity is noticed, if an account is compromised, or if a user leaves the company.
Microsoft Cloud App Security
If you are an admin on a Microsoft 365 account, you can access cloud app security at portal.cloudappsecurity.com. If you do not have it enabled, you will automatically be taken to the Office 365 Security & Compliance Center to turn it on.
Cloud App Security lets you see activity and files across all of your cloud apps. Including non-Microsoft cloud products. This includes activities from users such as opening, copying and sharing files or logging into cloud services. It also lets you see files across all cloud locations and set policies for those files right from the Cloud App Security Investigate Tab.
Applying and Using Policies in Cloud App Security
By setting up policies, Cloud App Security can scan through all of your files in all of your cloud instances to find controlled data ranging from Credit Card Numbers and Social Security info to Drivers License numbers. Additionally, you can configure automatic actions to be taken when this data is detected. You can make files private, email managers, remove external shares, and even transfer file ownership to a specific user. Most useful is to apply classification labels.
Classification Labels in Cloud App Security
Cloud App Security Classification Labels can have their own policies applied to them. Content Inspection allows you to use pre-configured expressions such as Health Insurance Claim Numbers, Date of Birth, Band Routing Numbers, and more. Custom expressions can also be created, such as specific Court Case Numbers.
Cloud App Security Alerts
Once your policies are in place, Cloud App Security has an Alerts tab that notifies you about risky, anomalous, or unauthorized behaviors like mass downloads, attempts to copy files to unmanaged devices, and files being shared with a personal email address. Just like in our Azure Security Center Demo, these can be sorted by severity, but can also be sorted by application, resolution, and date.
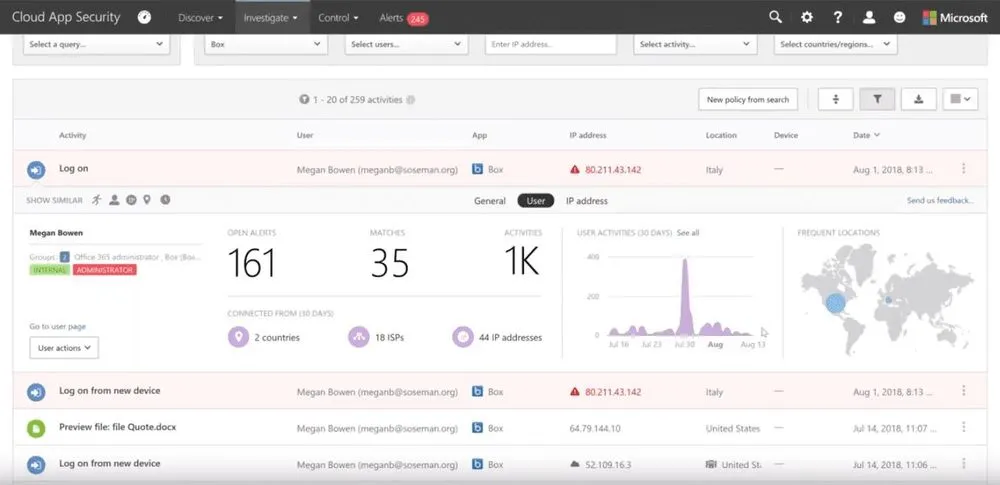
Cloud App Security Activity Log
From the activity log, under the investigate tab you can filter by application, user, IP address and activity type. This allows you to investigate suspicious activity in multiple ways. For example, if you see a anomalous login from a new device in one app, you can filter across all app by that IP device to see what other resources may have been accessed. In the demo, Matt identifies out-of-country access from a tor browser through an anonymous proxy.
End User Experience in Cloud App Security
Closing out the demo, Matt logs into his GMail account and shows how Cloud App Security uses Microsoft Azure AD to protect access. The login screen has been customized, making it easy to identify Phishing and impersonation attacks, as well as requires multi factor authentication. Matt then goes into GMail and tries to download a sensitive file that was protected by the policies he showed off earlier. Rather than a download, he gets a warning email that the file can’t be downloaded to an unmanaged device.
Get a Demo Of Cloud App Security
Agile IT has 15 Gold Competencies, including Cloud Security. If you’d like to find out how Cloud App Security can help protect your business contact us, or book a meeting with a Cloud Services Advisor.





