
The Spooky Thirteen Scariest Breaches and Hacks of 2018
Dont be afraid of cyber security The number of breaches and hacks in 2018 might seem scary but security tools are advancing almost as quickly as th...
Explore related topics in this category

Dont be afraid of cyber security The number of breaches and hacks in 2018 might seem scary but security tools are advancing almost as quickly as th...

Moving your data and applications to the cloud is one thing Maintaining compliance too is something else altogether and many SMBs and organizations ...
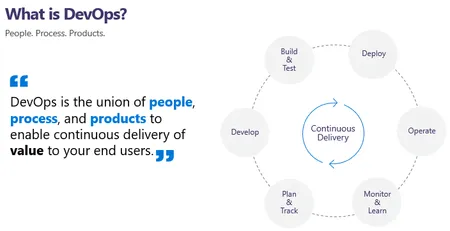
Using Azure DevOps for IT Management - Leverage Azure DevOps for effective IT management, automating processes for building, continuous testing, and deployment, even if you're not part of a software development team....

Businesses that deal in healthcare know the importance of HIPAA and HITECH compliance Violations of the privacy and security rules can result in larg...
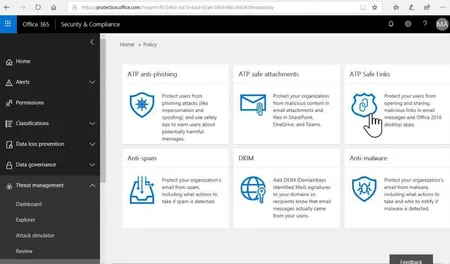
Phishing attacks are the most common method of credential theft, with a low barrier to entry (You don't need to know much more than how to make a web page and write an email) and ever increasing sophistication. This morning, one of our ...

The patches that companies release for their products enhance the security and functionality However this does not make them any less of a hassle A...

As explored in detail in Part 1 of this Zero Trust Security series the standard castle-and-moat, perimeter-styled network defense has been rendered practically useless in this new era of cloud computing, mobile devices, IoT, and other technologies...

Microsoft has been revamping all aspects of its Skype line The biggest change is in Skype for Business It isnt going away yet but Microsoft is str...

Remote work is more popular than ever According to the stylefontweight 400Bureau of Labor Statisticsstylefontweight 400https...
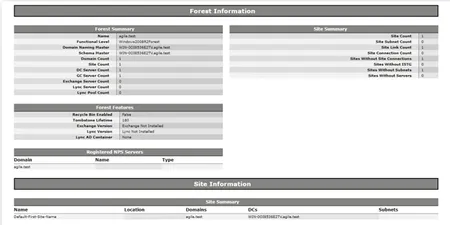
Active Directory Health Checks were the topic of September 20th's Agile IT Tech Talk, where we welcomed Miguel Escalante, the new Cloud Solutions Engineer on the Agile IT Team. Joined by Conrad Agramont, the two discussed how to identify an ailing Active Directory, what causes specific faults, and how to fix them...