
How to Find Shadow IT in Your Organization
To keep your networks secure you need to know about everything thats on them The two leading items on the Center for Internet Securitys list of ...
Explore related topics in this category

To keep your networks secure you need to know about everything thats on them The two leading items on the Center for Internet Securitys list of ...

Explore the transformative role of IoT in modern workplaces. Watch our video to understand the impact and benefits of IoT integration
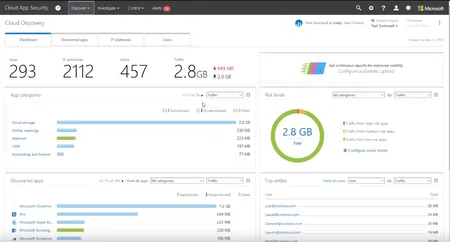
Learn how to tackle shadow IT using EMS and Cloud App Security in Agile IT's video, offering insights into identifying and managing unauthorized IT practices.
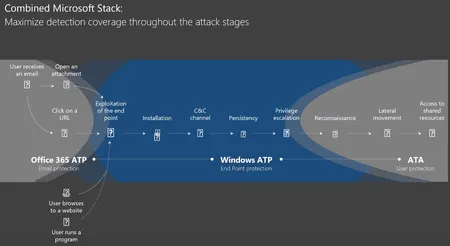
Uncover key strategies to defend against ransomware and rapid cyberattacks with Agile IT's video, highlighting Microsoft's advanced security solutions.

As we addressed a previous post, Microsoft Office 365 is a secure cloud-based platform for information and document management, providing a comprehensive overview of Microsoft cloud services...

Cloud software is taking over everywhere with lots of good reasons Software publishers are looking into shifting their business model Some want to...

UPDATE On May 24th the FBI announced that they had removed Photobucket images that were used to hide VPNFilter command and control IP addresse...

In the digital age where all paperwork records and ongoing projects take place on local and cloud networks nothing matters more than cybersecurity...

For organizations of any size data issues can range from problematic to downright devastating Lost or stolen data has the potential to sink your op...

Data travels everywhere Customers employees partners and vendors collaborate continuously on different devices and applications But is the data al...
Fill out the form to see how we can protect your data and help your business grow.
Discover more about Agile IT's range of services by reaching out.
Don't want to wait for us to get back to you?
Schedule a Free Consultation
Agile IT Headquarters
4660 La Jolla Village Drive #100
San Diego, CA 92122
Discover more about Agile IT's range of services by reaching out
Schedule a Free Consultation