
Pentesting Microsoft Office 365
IT security is a game of cat and mouse Bad actors are continuously developing new methods for disrupting systems and CTOs CIOs and their teams are ...
Explore related topics in this category

IT security is a game of cat and mouse Bad actors are continuously developing new methods for disrupting systems and CTOs CIOs and their teams are ...

WHAT IS A BREAK GLASS PROCEDUREYouve probably spotted breakglass points or boxes in a building Usually smashing the glass allows quick acc...

The business world is constantly chasing compliance With an everevolving litigation system and an increasing number of regulatory bodies prepared t...
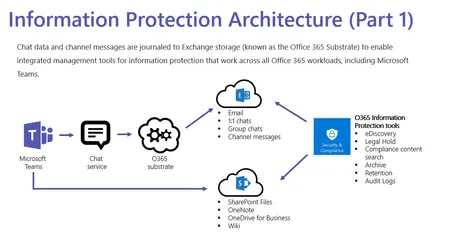
Compliance in Microsoft Teams is built upon the same Office 365 services that have been verified across many international, industry and regional standards, and setting up compliance in Microsoft Teams is part of Office 365’s...

Every organization has data and cyber security policies This is a nonnegotiable protection that companies rely on to maintain privacy over intellect...

Setting up SSO in Azure Active DirectorySSO in Azure active directory is the perfect balance of convenience and security Enabling it remove...

Dont be afraid of cyber security The number of breaches and hacks in 2018 might seem scary but security tools are advancing almost as quickly as th...

Moving your data and applications to the cloud is one thing Maintaining compliance too is something else altogether and many SMBs and organizations ...

Businesses that deal in healthcare know the importance of HIPAA and HITECH compliance Violations of the privacy and security rules can result in larg...
Phishing attacks are the most common method of credential theft, with a low barrier to entry (You don't need to know much more than how to make a web page and write an email) and ever increasing sophistication. This morning, one of our ...