Setting up Single Sign-On (SSO) in Azure AD (VIDEO)
Setting up SSO in Azure Active DirectorySSO in Azure active directory is the perfect balance of convenience and security Enabling it remove...

Setting up SSO in Azure Active Directory
SSO in Azure active directory is the perfect balance of convenience and security. Enabling it removes an attack surface, since your employees do not need to remember extra passwords, while their daily routine is streamlined, as they are seamlessly logged into their applications.
Why Use SSO?
- Simplicity - Provides a seamless experience for your employees, faster access to their applications, and ends password fatigue.
- Security - No more weak or duplicated password, single point of control, a unique and secure identity.
- Compliance - Helps admins increase control over the data users have access to and aids in HIPAA, SOX and NIST compliance.
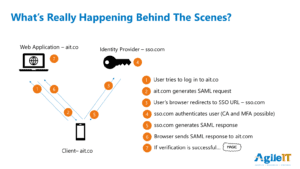
How Single Sign-On Works:
Instead of using a username / password combination, SSO uses a central trusted source of authentication to provide tokens that give access to other applications.
- User tries to log into an application from their browser.
- The application generates a SAML request and sends it to the user’s browser.
- The user’s browser sends the request to the identity provider.
- The identity provider authenticates the user.
- The identity provider generates a SAML response (token) and sends it back to the user’s browser.
- Browser sends token to the application.
- The application verifies the tokenized credential and grants access.
Authentication Scenarios of SSO Applications?
-
1.None
- Essentially mandating the use of shared passwords on apps.
2.Per User Password Extension/Addon (LastPass, Roboform, native browser)
- Typical – User has combination of personal and work passwords.
3.Enterprise Password Extension/Add-on (Centralized management)
- Can assign credtials to user or groups
- Allows changing of shared account credential to happen rapidly
4.SAML or Native Azure AD/Office 365 authentication
- Note – Only option that can stop sign-on of app when user is disabled in Azure AD.
Portal Scenarios
- None – Users get invites to apps in their email
- Intranet Webpage – Catalog of links on a singe page, or broken down in department (if lucky).
- Enterprise Portal – Users see ONLY web apps that they have access to.
- Unified Portal – Users see web apps, intranet apps (proxied internally, authenticated first in cloud), and Remote Desktop apps on one unified portal.
Provisioning Scenarios of SSO
- Manually – Create user in App on onboarding. Delete user on offboarding.
- SAML Add - Apps that provision user on first logon (if configured in app) will take the first/last name in the SAML request and use that to provision a new account.
- Note 1 - This is rarely with app vendors, so not a typical scenario.
- Note 2 - While user can’t logon, their account still exists in the app isolated admin portal. Per user fees charged.
- SCIM – Provisioning and De-provisioning (user account deleted from app after 30 days of being deleted on Azure AD).
- Note - Only about 20 vendors currently supporting (Salesforce, G Suite, Docusign, etc).
The Admin Experience
- Fast to onboard and offboard users.
- Time spent configuring SSO with vendors is saved during user tasks.
- Vastly improved security, compliance and monitoring. (see previous Tech Talks from Matt Soseman and Kevin Martins)
- Auto provisioning with SCIM (Simple Cloud Identity Management)
The SSO Demo
- Agile IT End User Experience
- MyApps Enterprise App portal settings in Azure
- Tour of App Examples in Azure:
- Individual Passwords End User Experience (Zapier)
- Shared Passwords distributed to group (No end user demo)
- SAML Logon (Bonusly)
- SAML Logon (Expensify) – Not all app vendors properly support “SSO”. It’s more like 1.5 vs single (1) sign on.
- SAML + SCIM (Docusign)
- Internal Application Proxy (PRTG)
About Agile IT Tech Talks
Agile IT Tech Talks are weekly sessions where we bring in subject matter experts for short, highly focused educational segments, followed by up to an hour of open Q&A where Agile IT clients can discuss their own environments with our engineers and a group of peers. While we release the demos and sessions on our blog, the Q&A benefit is only available to Agile IT Managed Service and Cloud Service Customers. Agile IT is a four time cloud partner of the year and offers fully managed security as a service. To find out more, schedule a free call with a cloud service advisor.





