Phishing Attack Simulator with Microsoft Security Center (VIDEO)
Phishing attacks are the most common method of credential theft, with a low barrier to entry (You don't need to know much more than how to make a web page and write an email) and ever increasing sophistication. This morning, one of our ...
Microsoft 365 Advanced Threat Protection - Phishing Attack Simulator
Phishing attacks are the most common method of credential theft, with a low barrier to entry (You don’t need to know much more than how to make a web page and write an email) and ever increasing sophistication. This morning, one of our contacts on Twitter revealed an example phishing attack page that looked identical to the the web version of Excel that was being used in attacks that spoofed a supply chain invoice email.
On a broader scale, phishing and other credential theft attacks are growing at an incredible pace. Thankfully Office 365 Advanced Threat Protection not only has robust phishing protection tools, there is also a Phishing Attack Simulator tool that allows you to run mock attacks on your own users to determine their vulnerability to any attacks that slip past your defenses.
In this week’s Agile IT Tech Talk, we were joined again by Microsoft’s resident phishing expert, Kevin Martins who talked about types of phishing, how to configure your Microsoft 365 Security Center to identify phishing attacks and stop them, and how to quickly set-up and launch a phishing exercise with the phishing attack simulator tool.
Phishing Attack Trends
Challenges to Defense
- Identity-based attacks are up 300% this year.
- 96% of malware is now automatically polymorphic (mutates constantly to avoid hash based detection).
- Most enterprises report using more than 60 security solutions. Which actually increases your attack surface.
Top Three Attack Types By Impact
- Password Spray - 200,000 accounts compromised just in August 2018.
- Phishing - 5 billion emails blocked in 2018, 44 million risk events in august 2018.
- Breach Replay - Use of leaked and stolen credentials. 650,000 accounts with leaked credentials in 2018.
Phishing Statistics - An Evolving Threat Landscape
- $12 billion lost to Business Email Compromise (BEC) scams since 2013
- 300,000 phishing campaigns analyzed in 2018
- 20% of clicks occur in the first 5 minutes
- 8,000,000 suspicious BEC attempts in 2018
Phishing Attack Delivery / Exploitation
Types of Credential Theft Attacks
- Password Spray (The use of common passwords tried against a list known account usernames)
- Leaked / Reused Credentials (Use of credential stolen from another site to check for reused passwords)
- Spoofed Domains (Use of “domain doppelgangers” that look similar to legitimate domains)
- Malicious Links (Using compromised sites or spoofed domains to deliver malware)
- Malicious Attachments (Use of malware or malicious documents)
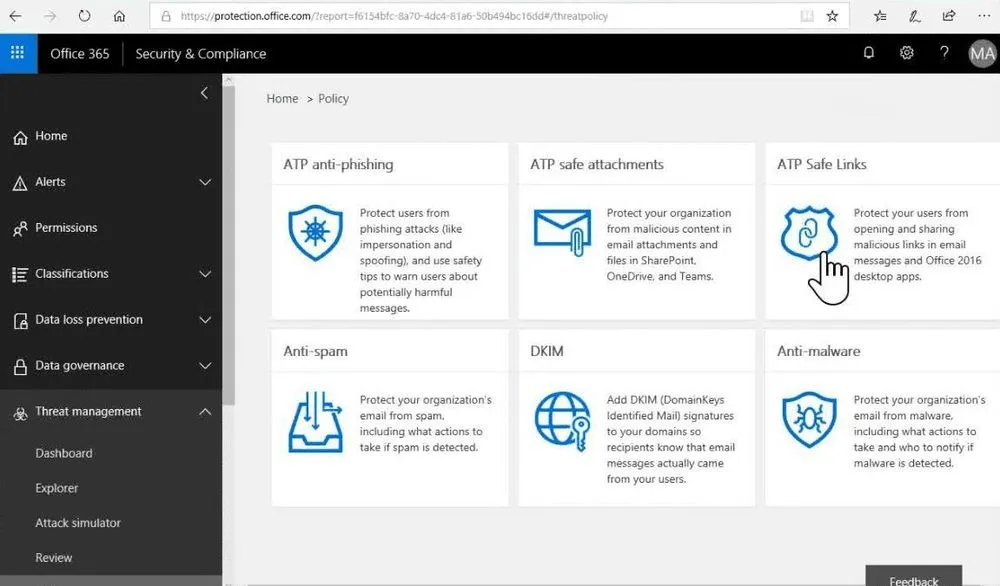
Advanced Threat Protection - Anti-Phishing
How to Configure Advanced Threat Protection’s (ATP) Anti-Phishing Policies
- Go to protection.office.com (You need to be an admin to get at the good tools.)
- Click “Threat Management” in the left sidebar menu
- Select “Policy” on the drop down that appears
- Click “Anti-Phishing” in the main window
From here you can manage and create policies. You should absolutely have an ATP policy in place for all users that defends them against known phishing attacks. However, given the prevalence and risk involved in targeted attacks including spearfishing and Business Email Compromise scams, you should create a second policy that is in place for your executive teams and anybody with financial signing ability within the company, as they are the most vulnerable.
You can set your policy priorities to set the order in which they are applied, with 0 being applied first.
You can view and edit each policy by clicking on it.
Editing ATP Phishing Policies
From the edit screen you have access to the following settings
- Policy name
- Description
- Who the policy is applied to
- Impersonation Protection
- Which users to protect
- Protect all your owned domains
- Which additional specific domains to protect
- Action to take if a user is impersonated in an email (Delete, Quarantine, Move to junk folder)
- Action to take if a domain is impersonated in an email (Delete, Quarantine, Move to junk folder)
- Should safety tips be displayed in the user’s email client if impersonation is detected?
- Spoofing Protection
- Enable or disable anti-spoofing protection
- Action to take if spoofing is detected (Delete, Quarantine, Move to junk folder)
- Advanced settings
- Advanced phishing thresholds
Advanced phishing thresholds let you determine how aggressive ATP should be in identifying potential phishing emails. Since more aggressive settings will result in more false-positives, the best practice here is to set phishing emails to go to quarantine and gradually adjust the threshold until false positives are minimized.
Advanced Threat Protection - Phishing Attack Simulator
The phishing attack simulator allows you to test your own users in order to evaluate their security awareness, the effectiveness of security training, or as part of exercises to remind employees of the importance of vigilance. While setting your phishing policies is a great start to defending your users against credential theft, using the attack simulator helps the human targets of attacks become more savvy and defensive.
In addition to the Phishing Attack Simulator, security center has password spray (Common passwords) and brute force (dictionary) attacks you can check against to make sure your user account’s are safe. One of the great benefits of the Phishing Attack simulator in ATP is that it is a Microsoft tool, and will not be stopped by Microsoft’s anti-phishing tools. Most third party tools require the creation of special white-listing rules. This can potentially open new attack vectors and requires additional time to configure. Launching an attack using ATP takes less than five minutes.
Launching a Spear Phishing Attack in Advanced Threat Protection (ATP)
- Go to protection.office.com
- Click “Threat management” on the left hand menu
- Select “Attack simulator” in the drop down
- Click “Spear Phishing Attack in the main window.
- Name your attack
- Click “Select template”
- Select a template
- Click Next
- Select Targets to attack
- Click next
- Set up your email details
- From (Name)
- From (Email) (Note: you can create a fake address in your system so it resolves to make the email look more real)
- Phishing Login Server URL (Microsoft provides one with the templates)
- Custom Landing page URL (When a user supplies credentials to the page, they are sent to page explaining the test. Use this setting to use your own URL.)
- Subject
- Click next
- Edit your template with either the WYSIWYG or using HTML source.
- Click next
- Then click “FINISH” to attack your users.
What the Attack Looks Like
The Phishing Email (Click to expand) 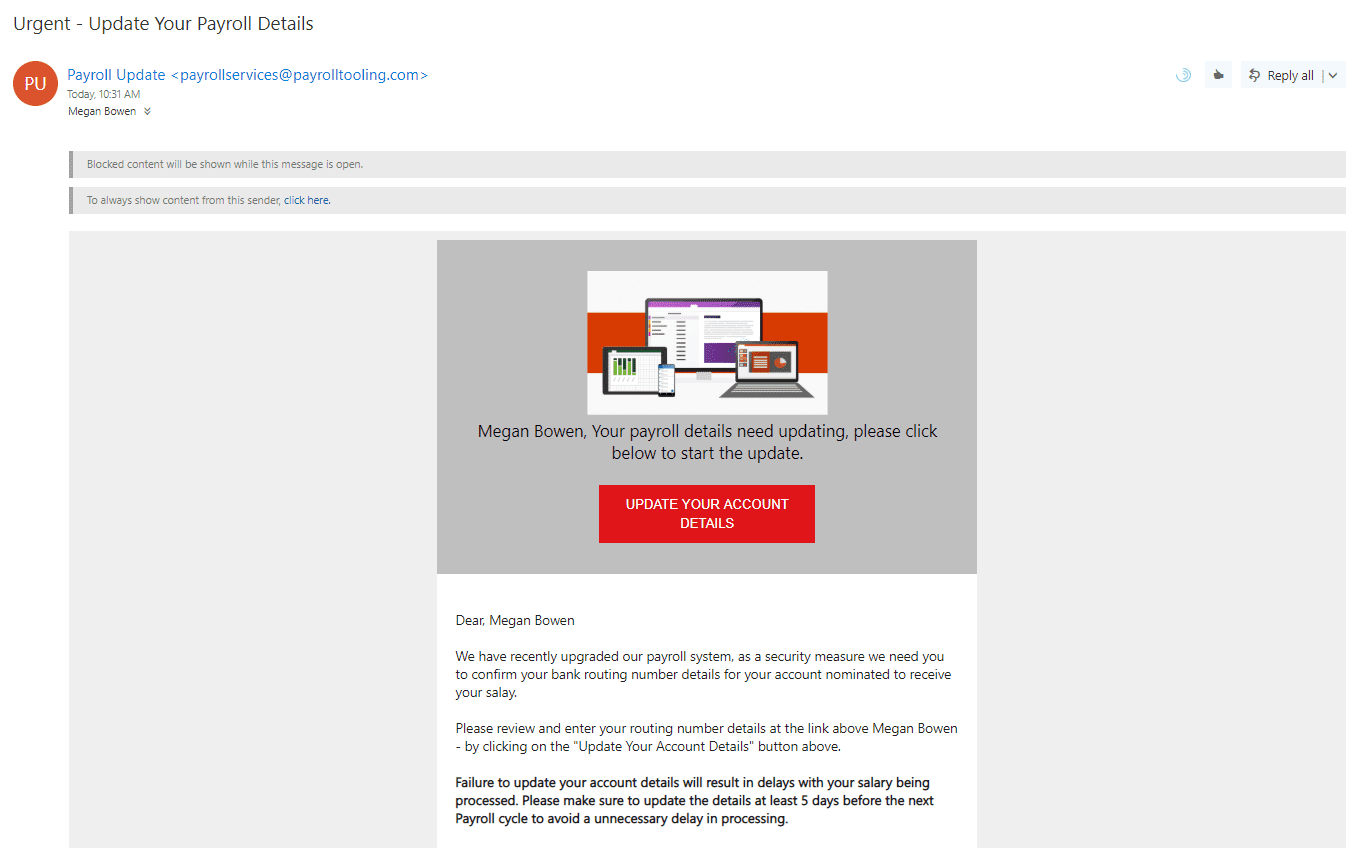 The Phishing Attack Website (Click to expand)
The Phishing Attack Website (Click to expand) 
The Results
To view the results of your exercise, go back to the attack simulator tab in the security and compliance center. Once the attack is launched, you get notification that the attack was completed and a link to view your report appears. This report provides:
- Total users targeted
- Successful attempts (If the users click the link, but do not input their credentials, it does not count as a success, but it does show the link clicked in the report)
- Success rate (This is the % of users who gave up their credentials, not the percentage of those who successfully recognized a phishing scam)
- A list of compromised users
- Email Address
- Time the phishing link was clicked (see who stopped before supplying credentials)
- Time that credentials were given (Entering garbage credentials will report as a positive)
Additional Phishing Resources
Kevin is literally writing the book on Phishing, which you can read at his Cloud Ready blog on Microsoft’s Technet. There you will learn a variety of skill ranging from enabling MFA to determining who is phishing your users. If you are aching to get your first phishing exercise started, he has a separate blog with Phishing Attack Example Templates you can use.
About Agile IT Tech Talks
Agile IT Tech Talks are weekly sessions where we bring in subject matter experts for short, highly focused educational segments, followed by up to an hour of open Q&A where Agile IT clients can discuss their own environments with our engineers and a group of peers. While we release the demos and sessions on our blog, the Q&A benefit is only available to Agile IT Managed Service and Cloud Service Customers. Agile IT if a four time cloud partner of the year and offers fully managed security as a service. To find out more, schedule a free call with a cloud service advisor.





