
How I Learned to Stop Worrying and Love Shadow IT
Shadow IT The phrase strikes fear in the hearts of IT managers People are introducing software and devices which you dont know about How can you...
Explore related topics in this category

Shadow IT The phrase strikes fear in the hearts of IT managers People are introducing software and devices which you dont know about How can you...
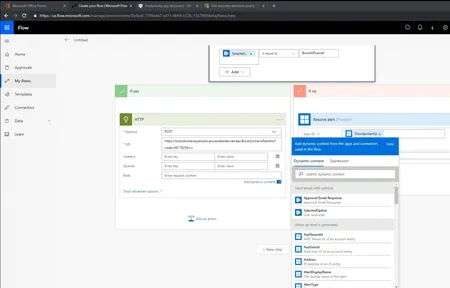
Automating Security with Cloud App Security and Microsoft Flow. In this Tech Talk we are once again joined by Microsoft Technical Solutions Archi...
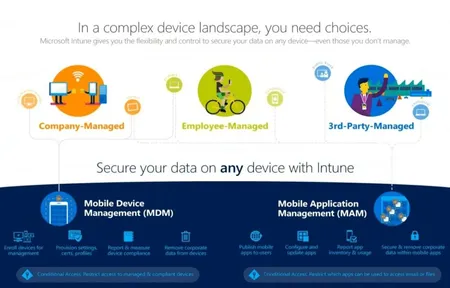
Intune for Mobile Device Management (MDM) and Mobile Application Management (MAM). Using Microsoft's Intune for Mobile Device management is a easy way to enable your mobile workforce while still maintaining control of your...

People in IT know the importance of security training If employees dont know how to avoid crucial mistakes the result could be an expensive breach...

One thing is certain for the cybersecurity world in 2019 there will be lots of online attacks and a large part of it will use new techniques Some k...

Stopping spoofing before it gets to your users becomes more important every day. Phishing is still the most common source of attacks, including malware, BEC scams, and ransomware. Providing defenses to stop spoofed and phishing emails t...

The Best Tech Talks of 2018When we decided to reformat our Tech Talks engineering office hours back in June we had no idea what to expect W...

Its not just Santa coming through your chimney this holiday season If youre not careful unwanted guests may look to enter as well taking physical...
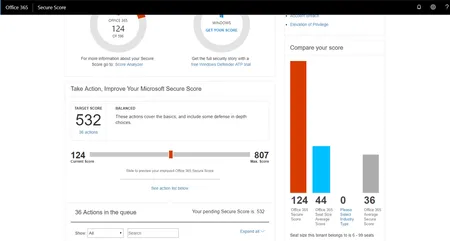
Managing Microsoft Secure Score VideoManaging Microsoft Secure Score is a simple transparent way to manage the security of your Office 365 W...

Kali Linux in Microsoft Azure VideoKali Linux is one of the most versatile and highly regarded pentesting platforms available The suite of ov...