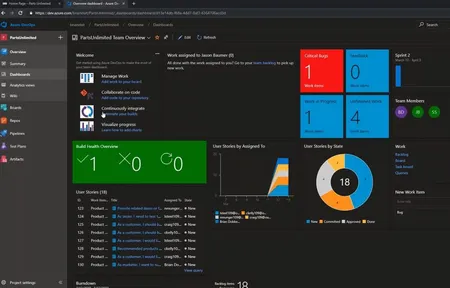
Inside Azure DevOps Demo (Video)
Inside Azure DevOpsThis week we took a rapid fire demo inside Azure DevOps and introduced two new guests the minds behind our Agile DevOps se...
Explore related topics in this category

Inside Azure DevOpsThis week we took a rapid fire demo inside Azure DevOps and introduced two new guests the minds behind our Agile DevOps se...

Most people who know about Git think of it as a repository for software projects Its actually more than that Its valuable with any kind of files ...

UPDATE Windows Virtual Desktop is now in General Availability Watch our Tech Talk to learn how to Set Up Windows Virtual Desktop news setting...

The DOD's JEDI Project has been awarded! The Pentagon's ambitions to create a robust government cloud structure has been the subject of debate, competition, and headlines. The Joint Enterprise Defense Infrastructure (or JEDI) project often reads more like a thriller than a project...
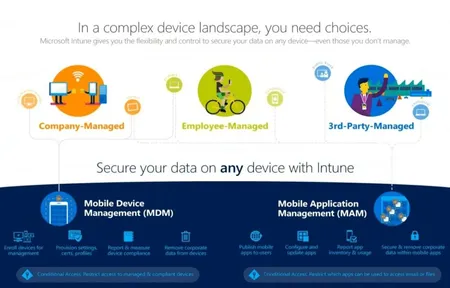
Intune for Mobile Device Management (MDM) and Mobile Application Management (MAM). Using Microsoft's Intune for Mobile Device management is a easy way to enable your mobile workforce while still maintaining control of your...

The NFL season wraps up today with Super Bowl LIII Were seeing more referees using the Microsoft Surface Pro Theyre able to watch instant replays...

January 14 2020 is approaching and for organizations everywhere that means one thing its time to start the process of migrating Exchange 2010 to 2...
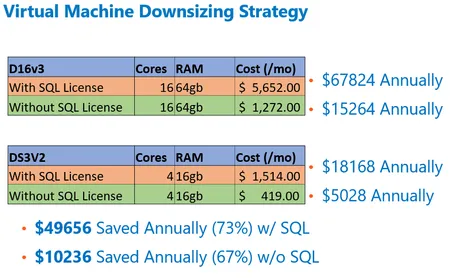
Saving Money in AzureSaving money in Azure is as simple as getting rid of whitespace You pay for CPU underutilization in your virtual machines...

The Best Tech Talks of 2018When we decided to reformat our Tech Talks engineering office hours back in June we had no idea what to expect W...

Kali Linux in Microsoft Azure VideoKali Linux is one of the most versatile and highly regarded pentesting platforms available The suite of ov...