Intune for Mobile Device Management Demo (Video)
Intune for Mobile Device Management (MDM) and Mobile Application Management (MAM). Using Microsoft's Intune for Mobile Device management is a easy way to enable your mobile workforce while still maintaining control of your...
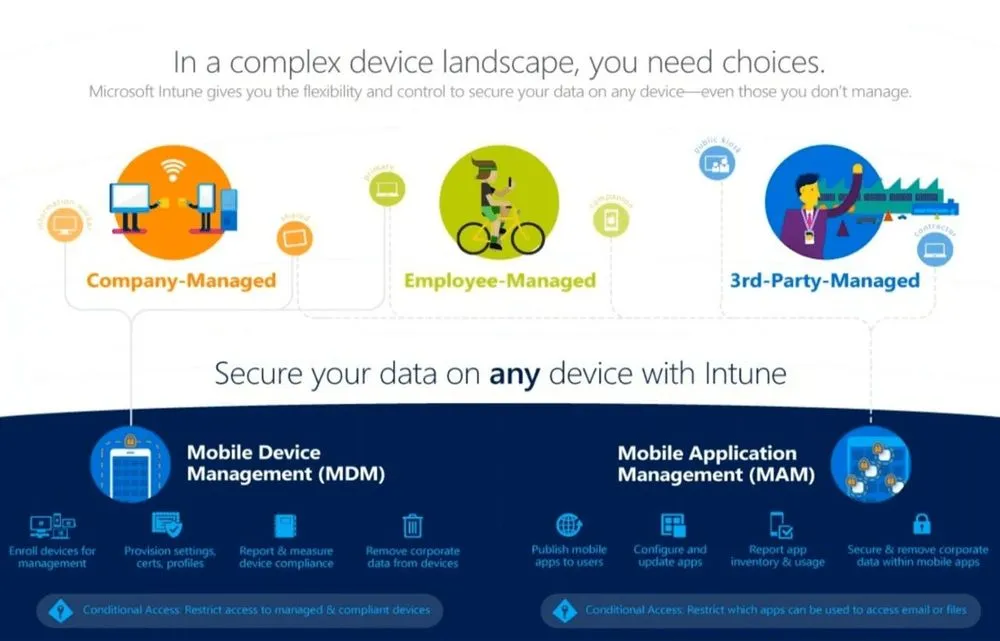
Intune for Mobile Device Management (MDM) and Mobile Application Management (MAM)
Using Microsoft’s Intune for Mobile Device management is a easy way to enable your mobile workforce while still maintaining control of your company data. Managing the mobile workforce is a constant balance act between productivity and security. One thing we have seen in many previous Tech Talks is how Microsoft Enterprise Mobility + Security (EMS) makes this an outdated conflict. In this Tech Talk, Matt Soseman, Microsoft Security Architect, discusses what Intune (Now part of Microsoft Endpoint Manager) is, what the user experience of managed devices looks like, and then walks through the admin interface to show how to configure Intune policies.
What is Microsoft Intune?
Microsoft Intune is Microsoft’s go-to solution for device management. Intune began in 2008 as Project Jupiter, in 2010, when Office 365 was first launching, it was a Silverlight based device management interface. It has come a long way since then, Intune can manage everything from Android and iOS mobile devices, to laptops and desktops running both Windows and MacOS. (Third party extensions are available to bring Linux machines into the environment.) It is offered via Azure and is bundled as part of EMS and Microsoft 365, but can also be purchased as a stand alone license. There is a limited version built into Offcie 365, but most features require do require the full Intune license.
What is MDM?
MDM stands for Mobile Device Management. MDM manages the entire device. It is used in educational environments where students are given laptops or tablets, with first line workers who may be using mobile devices in the field or warehouses or where employees are issued company owned devices. With MDM, you can:
- Factory reset a device
- Remove all data from the device
- Push applications to a device
- Manage device settings
- Lock down the device
- Disable / enable features like the device camera, screen shots, etc.
What is MAM?
MAM stand for Mobile Application Management and is mostly used in Bring Your Own Device (BYOD) scenarios where users bring their personal phones, tablets, or computers. In this case, applications are managed, but it does not touch the device itself. Instead, the applications themselves are managed. In this scenario, there are a number of different options available.
- Require a pass code to access managed apps
- Encrypt data in applications
- Restrict saving, copying, and pasting information from apps
- Managed web browsing
- Secure viewing of PDFs, images and videos
- Remotely remove data and access from the apps if the employee leaves the company
- Set device health requirements before a user is able to access those apps:
- Require a pass code and a mandatory lock period
- Enforce biometric locks
- Enforce minimum operating system versions
- Check device health using Windows Defender Advanced Threat Protection
Using Intune to Manage Workstations (PCs and Macs)
Intune allows you to also manage your workstations, including windows PC and Macs. Intune allows you to push applications and updates to any of your devices. This is connected with your active directory groups. Matt describes a compelling user experience where a company laptop is left behind in an uber. The employee buys a new computer at a local electronics store, signs in with their company credentials, and Intune automatically pushes down configurations, Office 365 apps, line of business apps, and security policies. There is no need for an image from the IT team, no need for the IT team to configure the device. Intune simply manages all the configuration of any new device.
Watch the Intune Demo
The actual demo begins at 16:33 with a demonstration of the end user experience of both MAM and MDM managed devices, then continues into the administration of Intune policies at 24:20.
About Agile IT Tech Talks
Agile IT Tech Talks are weekly sessions where we bring in subject matter experts for short, highly focused educational segments, followed by up to an hour of open Q&A where Agile IT clients can discuss their own environments with our engineers and a group of peers. While we release the demos and sessions on our blog, the Q&A benefit is only available to Agile IT Managed Service and Cloud Service Customers. Agile IT is a four time cloud partner of the year and offers fully managed security as a service. To find out more, schedule a free call with a cloud service advisor.





