Intune for Mobile Device Management Demo (Video)
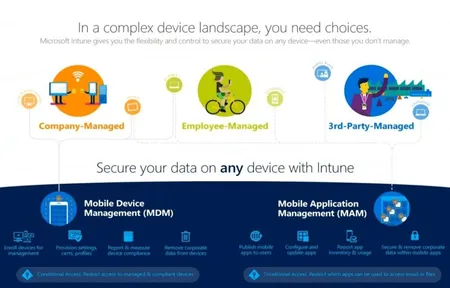
Intune for Mobile Device Management (MDM) and Mobile Application Management (MAM). Using Microsoft's Intune for Mobile Device management is a easy way to enable your mobile workforce while still maintaining control of your...