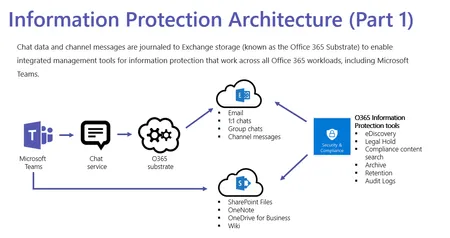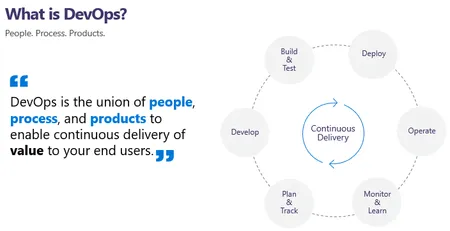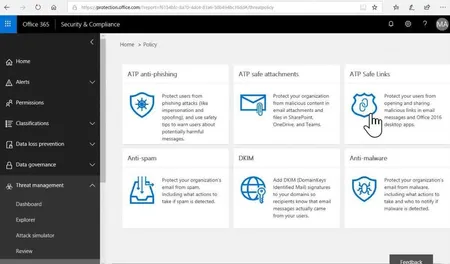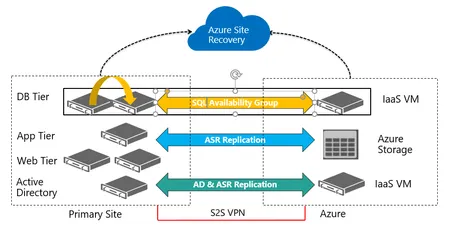
Performing Disaster Recovery with Azure Site Recovery
Performing Disaster Recovery with Azure Site Recovery. This week's Tech Talk focused on Disaster Recovery with Azure Site Recovery, and was a follow-up to Server Migration with Azure Site Recovery, ...