Managing Microsoft Secure Score (Video)
Managing Microsoft Secure Score VideoManaging Microsoft Secure Score is a simple transparent way to manage the security of your Office 365 W...
Managing Microsoft Secure Score (Video)
Managing Microsoft Secure Score is a simple, transparent way to manage the security of your Office 365, Windows and EMS environments. When you think about modern security, there are a lot of challenges. Identity attacks alone are up 300% this year alone and many attacks are going through identity because it is the easiest path to get at your information. With so many avenues for attack, it is difficult to know what to secure, what is secure and how to improve your security score. By providing visibility into you enterprise attack surfaces, Microsoft Secure Score helps you monitor, maintain and make improvements to your cybersecurity.
What is Microsoft Secure Score?
Originally called Office 365 Secure Score when it launched in February 2017 it expanded its focus across the entire Microsoft 365 enterprise suite (Office 365, EMS and Windows 10) in April of 2018 and became Microsoft Secure Score. Secure Score was envisioned as “a credit score for security”; a simple at-a-glance way to be sure that the proper security controls were in place in Office 365. Secure Score determines the Office 365 services you use (One Drive, Share Point, and Exchange), looks at your configuration and behaviors then compares it to a suggested baseline. If your configuration and behaviors are in line with best practices, you get points, which can be tracked over time. This gives you the ability to quickly determine what to do to reduce your risk.
How to Access Secure Score?
Secure score can be accessed in two ways:
- Go to SecureScore.Microsoft.com. (You must have admin privileges to view your secure score)
- There is also a Secure Score widget available in the Microsoft Security and Compliance Center that will take you to your Secure Score controls.
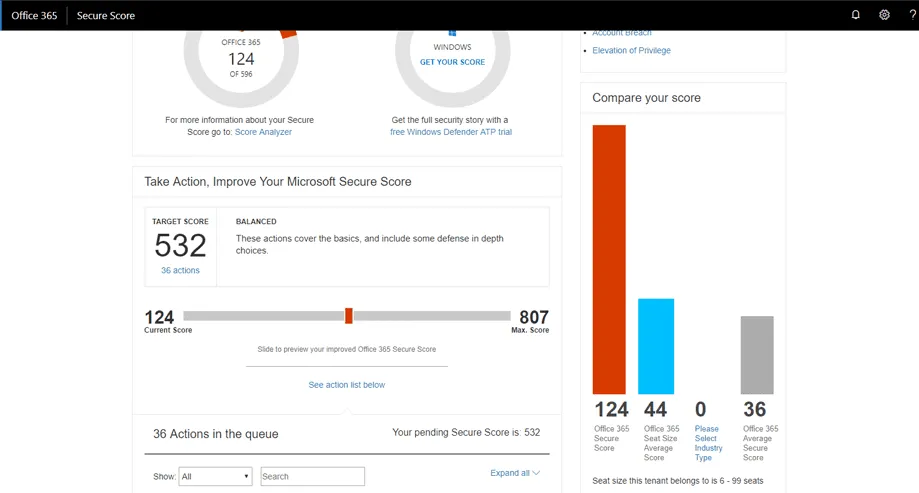
Understanding The Secure Score Dashboard
The secure score dashboard is a single-pane view of your security posture. What you see on the secure score dashboard once you log in are:
- The date of your current secure score. Secure Score is calculated every 24 hours at around 1 am PST)
- Your present secure score for Office 365 above your target score for comparison.
- Your present Windows Secure Score if you have Windows Defender ATP.
- A risk assessment widget that shows you what your attack risks are.
- A comparison widget that shows your secure score as compared to:
- All Office 365 tenants
- Other tenants of the same seat size as yours
- The secure score of other tenants in your industry.
- The Target Score Slider
Using Microsoft Secure Score’s Target Score Slider
The target score slider allows you to set your target score. By moving the slider to the left you lower your level of desired security, and moving it right increases it. As you move the slider, you will see your target score above go up and down, as well as the number of actions needed to be taken to reach the desired score. Below the slider is your action queue, a list of actions needed to be taken to reach the desired state.
Reading the Secure Score Action Queue
If you click the expand arrow to the right of each action item, you will get an in-depth view of the action needed. This view includes:
- A brief explanation of the action
- What category of defense the action impacts
- The user impact if implementing the change
- The predicted costs of performing the action
- Your score for the particular action
- The total score possible for implementing the action
- Threats that the action will reduce
- The compliance controls the action can affect
- Links to learn more about the control, ignore the recommendation, or to adapt the score for third-party applications.
What Suggested Actions are Available With Microsoft 365 Secure Score?
The actions available to you will vary based on the products and licenses in your particular tenant. Below is a complete list of all actions available with Microsoft 365 stack. This list is subject to change as new threats and capabilities are discovered or released.
| Name | Action Category | Action score | User Impact |
|---|---|---|---|
| Activate Information Rights Management (IRM) services [Not Scored] | Data | 10 | Low |
| Activate mobile device management services | Device | 20 | Moderate |
| Allow anonymous guest sharing links for sites and docs | Data | 1 | Moderate |
| Apply Data Loss Prevention policies | Data | 20 | Moderate |
| Apply IRM protections to documents | Data | 5 | Moderate |
| Apply IRM protections to email [Not Scored] | Data | 5 | Moderate |
| Automate log upload from firewalls | Apps | 5 | Low |
| Block Client Forwarding Rules [Not Scored] | Data | 20 | Moderate |
| Block jail broken or rooted mobile devices from connecting | Device | 1 | Moderate |
| Compile alternate contact info for all users | Identity | 1 | Low |
| Configure expiration time for external sharing links | Data | 2 | Moderate |
| Consume audit data weekly | Data | 5 | Low |
| Create a Microsoft Intune App Protection Policy for Android | Device | 10 | 10 |
| Create a Microsoft Intune App Protection Policy for iOS | Device | 10 | Moderate |
| Create a Microsoft Intune Compliance Policy for Android | Device | 10 | Moderate |
| Create a Microsoft Intune Compliance Policy for Android for Work | Device | 10 | Moderate |
| Create a Microsoft Intune Compliance Policy for iOS | Device | 10 | Moderate |
| Create a Microsoft Intune Compliance Policy for macOS | Device | 10 | Moderate |
| Create a Microsoft Intune Compliance Policy for Windows | Device | 10 | Moderate |
| Create a Microsoft Intune Configuration Profile for Android | Device | 10 | Moderate |
| Create a Microsoft Intune Configuration Profile for Android for Work | Device | 10 | Moderate |
| Create a Microsoft Intune Configuration Profile for iOS | Device | 10 | Moderate |
| Create a Microsoft Intune Configuration Profile for macOS | Device | 10 | Moderate |
| Create a Microsoft Intune Configuration Profile for Windows | Device | 10 | Moderate |
| Create a Microsoft Intune Windows Information Protection Policy | Device | 10 | Moderate |
| Delete/block accounts not used in last 30 days | Identity | 1 | Moderate |
| Designate less than 5 global admins | Identity | 1 | Low |
| Designate more than one global admin | Identity | 5 | 5 |
| Discover risky and non compliant shadow IT applications used in your organization | Apps | 20 | Low |
| Do not allow anonymous calendar sharing [Not Scored] | Data | 10 | Moderate |
| Do not allow calendar details sharing [Not Scored] | Data | 5 | Moderate |
| Do not allow external domain skype communications [Not Scored] | Data | 5 | Moderate |
| Do not allow mailbox delegation | Data | 1 | Moderate |
| Do not allow simple passwords on mobile devices | Device | 2 | Moderate |
| Do not allow users to grant consent to unmanaged applications | Identity | 10 | Moderate |
| Do not expire passwords | Identity | 10 | Moderate |
| Do not use mail forwarding rules to external domains [Not Scored] | Data | 1 | Low |
| Do not use transport white lists [Not Scored] | Data | 5 | Low |
| Enable Cloud App Security Console | Apps | 20 | Low |
| Enable Enhanced Jailbreak Detection in Microsoft Intune | Device | 10 | 10 |
| Enable Microsoft Intune Mobile Device Management | Device | Device | Moderate |
| Enable Password Hash Sync if hybrid | Identity | 10 | Low |
| Enable policy to block legacy authentication | Identity | 20 | Moderate |
| Enable self-service password reset | Identity | 5 | Moderate |
| Enable user risk policy | Identity | 30 | Moderate |
| Enable Windows Defender ATP integration into Microsoft Intune | Device | 10 | Low |
| Mark devices with no Microsoft Intune Compliance Policy assigned as Non Compliant | Device | 10 | Moderate |
| No transport rule to external domains [Not Scored] | Data | 5 | Low |
| Reduce mobile device password re-use | Device | 1 | Moderate |
| Register all users for multi-factor authentication | Identity | 20 | High |
| Remove TLS 1.0/1.1 and 3DES Dependencies | Data | 5 | Low |
| Require all devices to be patched, have anti-virus, and firewalls enabled [Not Scored] | Device | 10 | Moderate |
| Require all devices to have advanced security configurations [Not Scored] | Device | 5 | Moderate |
| Require MFA for all users | Identity | 30 | Moderate |
| Require MFA for Azure AD privileged roles | Identity | 50 | Low |
| Require mobile devices to block access and report policy violations | Device | 5 | Moderate |
| Require mobile devices to have minimum password length | Device | 1 | Moderate |
| Require mobile devices to lock if inactive | Device | 1 | Moderate |
| Require mobile devices to manage email profile | Device | 5 | Moderate |
| Require mobile devices to never expire passwords | Device | 1 | Moderate |
| Require mobile devices to use a password | Device | 5 | Low |
| Require mobile devices to use alphanumeric password | Device | 1 | Moderate |
| Require mobile devices to use encryption | Device | 1 | Moderate |
| Require mobile devices to wipe on multiple sign-in failures | Device | 1 | Moderate |
| Review blocked devices report weekly [Not Scored] | Device | 5 | Low |
| Review mailbox access by non-owners report bi-weekly | Data | 5 | Low |
| Review mailbox forwarding rules weekly | Data | 5 | Low |
| Review malware detections report weekly | Data | 5 | Low |
| Review permissions & block risky OAuth applications connected to your environment | Apps | 15 | Moderate |
| Set automated notification for new OAuth applications connected to your corporate environment | Apps | 20 | Moderate |
| Set automated notifications for new and trending cloud applications in your organization | Apps | 15 | Moderate |
| Set custom activity policy for your organization to discover suspicious usage patterns in cloud apps | Apps | 10 | Moderate |
| Set outbound spam notifications [Not Scored] | Data | 15 | Low |
| Set up Office 365 ATP Safe Attachments | Data | 15 | Moderate |
| Set up Office 365 ATP Safe Links to verify URLs | Data | 15 | Moderate |
| Set up versioning on SharePoint online document libraries | Data | 2 | Moderate |
| SPO Sites have classification policies [Not Scored] | Data | 10 | Moderate |
| Store user documents in OneDrive for Business | Data | 10 | Low |
| Tag documents in SharePoint [Not Scored] | Data | 2 | Moderate |
| Turn on audit data recording [Not Scored] | Data | 15 | Low |
| Turn on customer lockbox feature | Data | 5 | Moderate |
| Turn on mailbox auditing for all users | Data | 10 | Low |
| Turn on sign-in risk policy | Identity | 30 | Moderate |
| Use Cloud App Security to detect insider threat, compromised account, and brute force attempts | Apps | 15 | Low |
| Use non-global administrative roles | Identity | 1 | Low |
Agile IT Tech Talks are weekly sessions where we bring in subject matter experts for short, highly focused educational segments, followed by up to an hour of open Q&A where Agile IT clients can discuss their own environments with our engineers and a group of peers. While we release the demos and sessions on our blog, the Q&A benefit is only available to Agile IT Managed Service and Cloud Service Customers. Agile IT is a four-time cloud partner of the year and offers fully managed security as a service. To find out more, schedule a free call with a cloud service advisor, or REQUEST A QUOTE:
This demonstration provides a quick look at how a number of integrated tools across Microsoft’s security stack can be applied to enable a Zero Trust methodology in your organization. For more in-depth explorations and demos, please check out these other blogs: What is Zero Trust Security Zero Trust with Microsoft 365 Understanding Active Directory Microsoft Defender Advanced Threat Protection Demo Automate Security with Cloud App Security and Power Automate Intune for Mobile Device Management Managing Microsoft Secure Score Setting up Single Sign On (SSO) in Azure Active Directory Azure Information Protection Demo Protecting your Data Even Outside of Office 365 Azure Azure Security Center Demo Combating Shadow IT with EMS and Cloud App Security Need help defending your remote workers and assuring your devices, data, and identities are secure? Agile IT is a Gold Microsoft Security Partner, and have solutions to help your organization remain secure.





