
Improve Office IoT Security and Prevent Cyber Threats
Office IoT is a rising trend that shows no signs of stopping As the Internet of Things becomes increasingly popular in the consumer world its no s...
Explore related topics in this category

Office IoT is a rising trend that shows no signs of stopping As the Internet of Things becomes increasingly popular in the consumer world its no s...

Data travels everywhere Customers employees partners and vendors collaborate continuously on different devices and applications But is the data al...

Local Government Cybersecurity is grossly underfunded in state and local government agencies The average local government agency spends less than 5 ...

Happy New Year everyone2017 was a great year at Agile IT with our partners and customersWe committed to the cloud when we started the business o...

For an updated version of this guide please visit our Office 365 Workstation Setup and End User Workstation Configuration Guidenewsoffice3...

Is your business constantly playing catchup with compliance requirements Achieving and maintaining compliance for your cloudbased resources is a co...

Microsoft routinely adds new features and products to the Azure landscape to meet the growing needs of cloudbased companies If your organization rel...

Mobile email access is integral to business productivity But increased access means increased security riskMobile device management MDM secures...
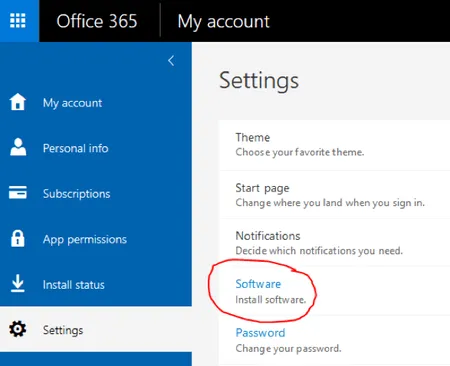
Youve purchased Office 365 licenses Now you need to install Office 365 and configure user workstations Fortunately Autodiscover automates many of ...

Your customers shop via mobile devices desktops wireless hotspots applications and other channels that put their data at risk To help secure your ...