Guide to Office 365 Mobile Setup and Device Management
Mobile email access is integral to business productivity But increased access means increased security riskMobile device management MDM secures...

Mobile email access is integral to business productivity. But increased access means increased security risk.
Mobile device management (MDM) secures, manages and monitors mobile devices across an organization. With more employees accessing email, documents and company data from their mobile devices, MDM enables IT managers to control devices and security.
Below is a guide to Office 365 mobile setup, including how to set up mobile access for users, manage devices and set up MDM rules Office 365.
The IT Admin’s Office 365 Mobile Setup Guide
Since Microsoft released all Office 365 apps for free on mobile devices, it opened new productivity opportunities for businesses.
Nearly every phone and tablet can be set up with Office 365 to send email, access your calendar and contact info and share documents on OneDrive and SharePoint. Most phones and tablets can be set up for Office 365, including iPhone, iPad, Android, BlackBerry and Windows phones.
How to Set Up Mobile Access for Your Users
To start, you need to set up user access. If you’re allowing employees to access email and Office 365 on their mobile devices, you can remotely manage phone features and options.
Turning Mobile Access On Or Off
Unless your business has specific compliance requirements, users can set up their own email on their mobile device once you grant them access.
Mobile access to email is turned on by default in most devices. As an administrator, you can control access through Exchange ActiveSync.
To change the default access settings for Exchange ActiveSync and turn off or suspend access, follow these steps.
- In the Office 365 portal, click Admin > Exchange.
- In the Exchange admin center, click Mobile.
- Under Exchange ActiveSync Access Settings, click Edit.
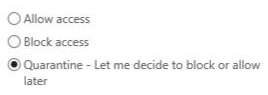
- In the Exchange ActiveSync access settings dialog box, choose one of the following:
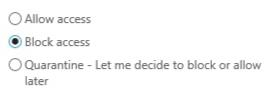
- Allow access
- Block access
- Quarantine — This puts the device on hold so you can decide to block or allow it later. Once you’ve enabled Exchange ActiveSync, you can manage devices and set up rules on the Mobile Device Access page.
Office 365 Mobile Setup With BlackBerry Business Cloud Services
For BlackBerry devices, you’ll need to enable BlackBerry Business Cloud Services to integrate email and calendar. Only global admins can enable BlackBerry Business Cloud Services.
-
Go to Admin > Service Settings > Mobile. Click Enable Service.
-
In the dialogue box, select Yes, then click OK.
-
You’re now back on the Mobile page. Select Manage to go to the BlackBerry Business Cloud Services website and set up your connection. To turn off BlackBerry Business Cloud Services, choose:
-
Admin > Service Settings > Mobile > Remove Service
Mobile Device Management in Office 365
If you’re setting up Office 365 for the first time, you can create MDM rules in Office 365 to control mobile devices.
If your organization already has devices set up with Office 365, you’ll need to go through each device to manage access. After setting up each device with the correct access, you can set up MDM rules going forward.
Office 365 Mobile Setup for Individual Devices
Here’s how to manage access for mobile devices that already have Office 365:
- Log into the portal.
- Navigate to the Exchange Admin Center (EAC.)
- Search for a user with a mobile device.
- Double click the mailbox to open properties. Then select Mailbox Features.

- Under Mobile Devices, click on View Details.
- Select the device you want to add, and click Allow.
- To block unwanted devices, highlight them and select Block.

How to Set Up Mobile Access Rules in Office 365
Because email access is turned on by default in most mobile devices, you’ll need to set up rules to block or quarantine unwanted devices.
Blocking Access
Blocking rules restricts access for all device models that aren’t specifically granted access. Here’s how to create general MDM rules to block devices for Office 365 mobile setup:
- Log into the portal.
- Navigate to the Exchange Admin Center (EAC.)
- Select Mobile.

- Select the + under Device Access Rules.
- Under Device Family, select Browse. Choose the mobile device, and click OK.
- Select the device model, and click OK.

- Select Block Access, and save your selection
How to Set Up Quarantine Rules
Quarantine rules allow you to put a mobile device “on hold” and block or allow it later.
To get started:
- Log into the portal.
- Navigate to the Exchange Admin Center (EAC.)
- Select Mobile.
- Select the + under Device Access Rules.
- Under Device Family, select Browse. Choose the mobile device, and click OK.

- Select the device model, and click OK.

- Select Quarantine and Save.
You can manage the devices in the Quarantine Devices view. The rule quarantines devices connected with Exchange ActiveSync that don’t have explicit access permissions set up.
Additional Office 365 Mobile Setup Resources
Once granted access, users can set up Office 365 on their mobile devices.
Review these resources to set up Outlook for mobile:
- Set up email on Apple iPhone or tablet
- Set up email on Windows phone or tablet
- Set up email on Android phone or tablet
Have more questions about Office 365 mobile setup? Schedule a call with us today.





