
Rapid Zero Trust Implementation With Microsoft 365 (part 1)
From cybersecurity insurance requirements to executive ordersnewsinsidethenewcybersecurityexecutiveorder and from NIST frameworksnews...
Explore related topics in this category

From cybersecurity insurance requirements to executive ordersnewsinsidethenewcybersecurityexecutiveorder and from NIST frameworksnews...

Stopping spoofing before it gets to your users becomes more important every day. Phishing is still the most common source of attacks, including malware, BEC scams, and ransomware. Providing defenses to stop spoofed and phishing emails t...

WHAT IS A BREAK GLASS PROCEDUREYouve probably spotted breakglass points or boxes in a building Usually smashing the glass allows quick acc...
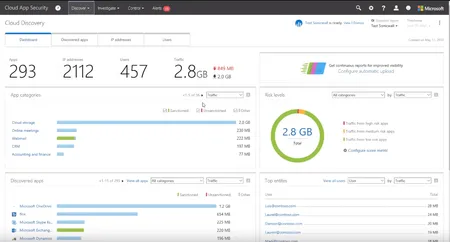
Uncover key strategies to defend against ransomware and rapid cyberattacks with Agile IT's video, highlighting Microsoft's advanced security solutions.