Rapid Zero Trust Implementation With Microsoft 365 (part 1)
From cybersecurity insurance requirements to executive ordersnewsinsidethenewcybersecurityexecutiveorder and from NIST frameworksnews...

From cybersecurity insurance requirements to executive orders and from NIST frameworks to CISA guidance, it is clear that Zero Trust is no longer just a buzzword. In the new post-COVID world of hybrid work, it is clear that the old school perimeter model of defense is gone for good, it’s walls shattered by a remote workforce that has come to expect the ability to work anywhere, at any time and on any device. Thankfully, rapid Zero Trust implementation is not only possible, if you are using Microsoft 365, it’s relatively painless to get started.
Stages of Zero Trust Implementation
- User Access and Productivity
- Apps and Data
- Security Operations
- Operational Technology
- Data Center Security
Note, that in some cases these stages can operate in tandem, however the logical separation makes implementation easier to understand.
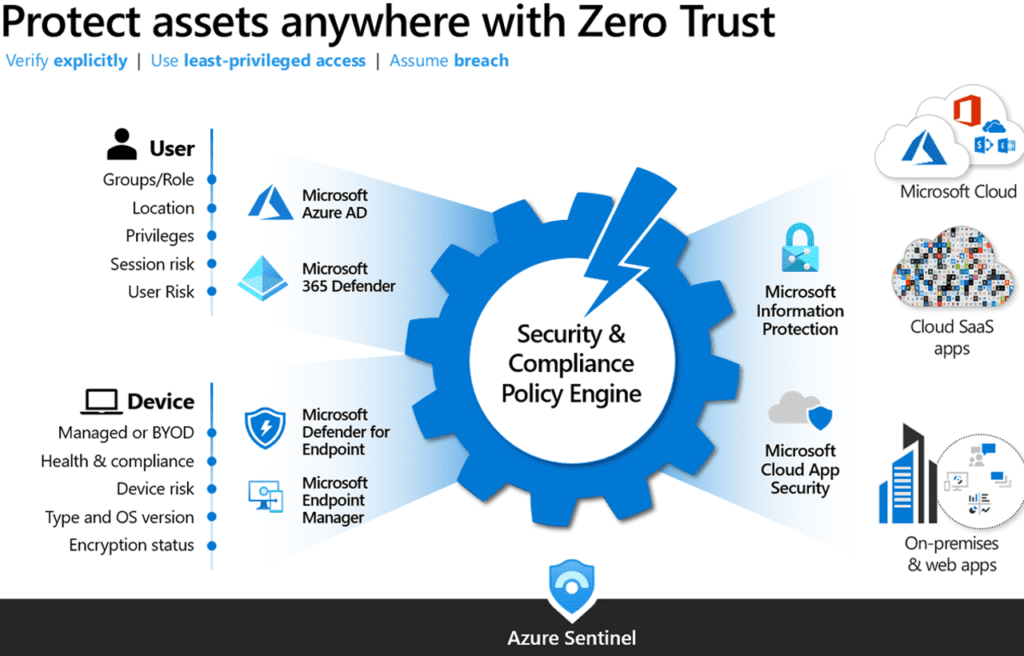
User Access and Device Security
User Account Security with Multifactor Authentication (MFA), Conditional Access, and Passwordless Authentication
The first thing to secure is user accounts. Passwords are increasingly vulnerable, so Multi-factor authentication is a must, and moving beyond password-only based verification is critical. Easing user impact with conditional access allows you to set rules where MFA is not required if they are logged into the local network, or to strengthen certain accounts such as admins by restricting their ability to log in to specific devices and locations.
Microsoft has recently rolled out the ability for users to completely remove their passwords from Microsoft 365, and the ease and simplicity of Windows Hello to use biometrics, PINs, and the Microsoft Authenticator app is accelerating the end of the password era.
Device protection with MDM and MAM
Once you have strengthened you user identity and access, the next step is to secure devices. With users often using their own devices to perform work, if their personal devices have been compromised it becomes possible for attackers to steal credentials and expand their attack against other parts of your environment. Intune, part of Microsoft Endpoint manager allows you to protect both company owned and private (BYOD) devices. To manage corporate owned devices, Mobile Device Management (MDM controls the entire device.
With Mobile Application Management (MAM) you only control your company information and applications on the device. With MAM If the device does not meet your established device health policies, such as recent updates, passcode length, screen lock time, you can restrict what information they are able to access, for example allowing them to view less sensitive information like product PDFs, while prohibiting them from accessing critical information such as financials, Personal Health Information (PHI), etc.
Application Protection
Now that your users identities and devices are protected, it is time to protect your applications and data. Azure AD (AAD) makes it easy to enforce the strong user access controls established with MFA and conditional access across all of your applications.).
To secure applications, you begin by configuring AAD for all of your SaaS applications using SAML, OAuth or OIDC. For applications that do not support these modern protocols, connect your VPN appliance to Azure AD Authentication. This expands your device and user validation from above to all of your VPN sessions. The next step is to move applications off of VPNs by publishing existing on-prem line of business and IaaS applications through Azure App Proxy. In addition to protecting the application, it also enables you to restrict accounts to accessing a single application, unlike traditional VPNs that frequently provide access to all ports and protocols across a network.
Data Protection
Microsoft 365 includes tools such as Microsoft Information Protection and Cloud App Security that can protect your information both inside and outside of Microsoft 365. As you focus on protecting your data, you should make sure that your information is secure no matter where it is stored; in cloud services such as Google Drive and DropBox, on USB devices, workstations, mobile devices. You should take a full-lifecycle governance approach to your information that includes
- Discovery
- Classification
- Protection
- Monitoring
Microsoft information Protection transparently encrypts data requiring identity authentication for access. Again, these controls can be a strict as you find necessary and based on predefined sensitivity labels. Microsoft Cloud App Security (MCAS) enables you to discover unstructured data across multiple cloud applications, and Azure Purview gives the ability to discover, protect, and govern structured data across your entire organization in SQL databases, Amazon S3 instances, Oracle DB and dozens of other data sources.
All together, these tools mean that even if information leaves your environment on a stolen device, snuck out in a peanut butter sandwich, or exfiltrated by an APT, it becomes unreadable without proper user authentication. This also means that when a employee leaves the company, no matter where they may have stored company information they lose access to it.
Security Operations (SecOps)
Usually run in parallel to user device and data protection efforts, modernizing SecOps is meant to increase the productivity, effectiveness and response times of security team members through strong prioritization to assure team members are focused on the most impactful threats to the organization and not chasing false alarms, struggling through divergent tools and missing signals in siloed platforms.
Azure Sentinel is a combined Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) Platform that collects signals, logs, and telemetry from just about everywhere.
The Key focuses for a SecOps team implementing Zero Trust are:
- Streamline Responses
- Master threat response and remediation on the most commonly attacked resources using:
- Extended Detection and Response
(XDR) Provide high quality alerts for new resource types, bypassing manual effort and delays when trying to build every alert in your SIEM.
- Streamlining the processes for these common attacks
. Focusing Tier 1 (triage) and Tier 2 (analyst) teams on mastering these attacks will recognize and stop both commodity and advanced attackers earlier in attack.
- Unify Visibility
– creating high-quality individual alerts from raw data in SIEMs is difficult, however, they are useful for bringing data and context together for investigations and threat hunting, giving a full view across your entire estate, making it harder for attackers to hide.
- Reduce Manual Effort -
Security operations should be focused on reducing manual and repetitive tasks like switching tools, typing commands, copy/pasting data, etc. Giving analysts a streamlined end to end integrated experience with SOAR technology increases effectiveness (and happiness). SOAR technology is built into both Microsoft 365 Defender and Azure Sentinel.
Leverage Agile IT for Zero Trust Implementation
Agile IT began implementing Zero Trust architectures for it’s clients in 2018, and has included core tenants into every migration and implementation we perform. To find out how you can defend you users, devices, data and infrastructure across any cloud. Request a free consultation.