Understanding Microsoft EMS
Employees need instant access to information to do their jobs fast and well Introducing Microsoft EMSAs more companies replace physical servers wi...
Employees need instant access to information to do their jobs fast and well. Introducing: Microsoft EMS
As more companies replace physical servers with flexible cloud environments, there’s one question on everyone’s mind: How do you protect this intellectual property & data?
In the past, you’d simply put permissions on a folder to prevent unauthorized access. But with the cloud, that will no longer suffice. Now, you need to protect data wherever it ends up and on company and personal devices.
The Cloud Security Solution: Enterprise Mobility Suite
While Office 365 offers baseline security protections, it recently rolled out the Enterprise Mobility Suite (EMS) to better track and control data as it moves across locations and devices. Agile IT partnered with Travis Liles, Partner Technology Specialist at Microsoft, to provide an overview of the EMS platform and its functionalities.
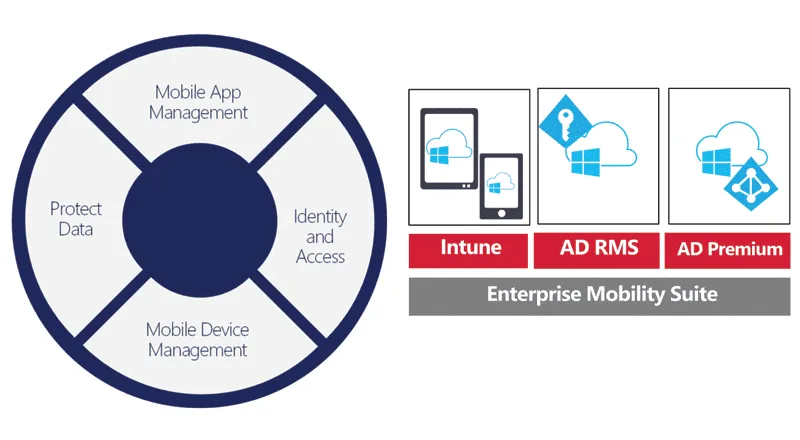
EMS encompasses the different layers of security you’ll need to protect critical data. In this article, we’ll discuss the 3 pillars of EMS, including:
- Unified Identity (Azure AD Premium) — Who is accessing data?
- Managed Apps & Devices (Intune) — Where are they accessing it?
- Data Protection (Azure Rights management) — How can you protect data, wherever it goes?
Control access with Active Directory Premium
Office 365 users already utilize Azure AD – their cloud directory – whether they realize it or not. Active Directory Premium allows you to synchronize on-prem Active Directory with cloud-based Active Directory to create a single identity and eliminate the need for multiple passwords. Having centrally managed identities and access provides benefits beyond the Office 365 platform. You can monitor and protect access to SaaS applications through multi-factor authentication (MFA) via email or text, app usage reports and alerting and also suspend MFA from unknown devices.
Ultimately, AD Premium helps ensure the right people have access to the right information on the right devices and empowers users to seamlessly (and safely) log into thousands of SaaS apps.
Manage Apps & Devices with Intune
Intune enables you to manage mobile devices and applications and protect data. You can assign conditional access to email and documents within Exchange and OneDrive for Business or deny access if a device falls out of compliance.
Intune also gives you the ability to enroll and manage corporate-owned devices through bulk enroll or large device deployments. When users get a new phone, they can simply insert their previous SIM card and access all that data instantly.
Protect data with Azure Rights Management
As your users access documents and apps from personal devices, you need to make sure documents are properly taken care of once they leave their environment. Azure Rights Management is one way to control who can see, open, read and edit documents on a granular level. Say you allow a user to open a document only. If he saves it to a USB and someone else tries to open it, it will ask for the original user’s credentials, leaving a digital paper trail.
Why Office 365 & EMS are better together
Office 365 offers base-level features, such as selective wipe and the ability to deploy apps and manage data device settings. When you add EMS, you get support for other mobile workloads & singe sign-on for 3,500 SaaS platforms (e.g., Salesforce, Reuters, etc.) Here are a few examples of the added security benefits you’ll receive:
- Mobile Device Management (MDM): MDM adds PC management, mobile app management, secure content viewers, certificate provisioning, compliance policies, conditional access and much more on top of baseline Office 365 features.
- Extended MFA: Just as users must provide additional security credentials when accessing Office 365, multi-factor authentication also extends to other SaaS apps.
- Information Protection: With EMS, you get protection for on-prem Windows Server file shares, email notifications when sharing documents, email notifications when shared documents are forwarded, Office integration, managed browser and more.
Make sure EMS works for your organization
Want to trial EMS before diving right in? AgileEMS is a production setup configured in your environment that provides the full EMS experience to admins and end users. You can see how EMS works in your workstation and effectively evaluate and plan for it once it’s applied to the entire organization. You’ll simply need 3 workstations, 2 non-PC devices and an existing Office 365 deployment to get stared.
For more information on AgileEMS, contact Agile IT today. To access the complete webinar, click here.





