
A Guide to Planning Zero Trust Architectures - Part 1
The days of castleandmoat cybersecurity are over At least theyshouldbe over The old model is no longer cutting itnot even close Across the...
Explore related posts tagged with "Cloud Cybersecurity"

The days of castleandmoat cybersecurity are over At least theyshouldbe over The old model is no longer cutting itnot even close Across the...

Cloud Services are Growing but are They SecureThe trends are clear Microsoft reported a98 percent yearoveryear revenue growthhttpsw...

Get essential tips to help detect hackers and prevent breaches, ensuring your business stays protected in the face of growing cybersecurity challenges.
Uncover key strategies to defend against ransomware and rapid cyberattacks with Agile IT's video, highlighting Microsoft's advanced security solutions.

Like most companies you might have some assets in the cloud to simplify file sharing offload expensive infrastructure or save on storage costs You...

The cloud enables you to log in anywhere with Internet access to retrieve your files without the fear of potentially losing physical removable medi...

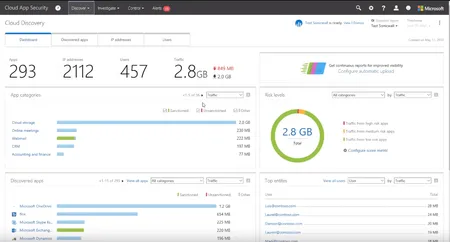
Security concerns have held many companies back from moving their infrastructure to the cloud As an IT security professional youre taught to always...

2017 is a promising year for new cloud app trends Many businesses have already taken the plunge and experienced how the cloud makes business run smoo...

When it comes to the cloud cybersecurity is first on every CEO and IT directors mind Thats what makes this National Cybersecurity Awareness Month ...