
Securing the Remote Workforce
In todays professional environment its never been more important to have a secure remote workforce There was a time when working remotely remained...
Explore related topics in this category

In todays professional environment its never been more important to have a secure remote workforce There was a time when working remotely remained...

Social engineering is by far the most insidious type of hack to ever be used against a business The worst part is that hackers arent even pitting th...

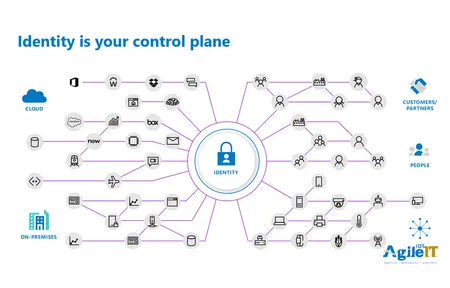
What is Zero Trust Security ZTSZero Trust Security was still considered a buzz word when we first wrote about over a year agonewsplannin...
![Microsoft Teams for Heathcare Demo [Video]](/_astro/teams-for-telemedicine.CVUnL4_X_ZicdsA.webp)
Microsoft teams is a valuable tool in any organization, but once you start looking at specific use cases, you start to see the real power behind the platform...

When you consider all the online threats out there (with phishing, Shadow IT, APTs, ransomware, and cryptominers, to name just a few), you must ensure you are employing necessary and effective tools capable of protecting....

In so many industries cloud computing has revolutionized the way we store files and work in the digital space Its not just convenient it also help...
In this Tech Talk Conrad Agramont Agile IT CEO discusses the seven types of Active Directory what to use them for and how they can be used togeth...

The National Security Agency has released a document on "Mitigating Cloud Vulnerabilities" to the public. It addresses the security risks that are distinctive to cloud services...

ITAR DFARS DIB CMM , CMMC , FCI , CUI , ATP , AOS-G , AOS-G . After a few months of working in any specialized area, particularly within the DoD ...

The Department of Defense has just released Version 1.0 of CMMC , the Cybersecurity Maturity Model Certification program. It will provide the basis for ensuring compliance under ...