Best Practices on Windows DNS Scavenging
Scavenging will help you clean up old unused records in DNS Since clean up really means delete stuff a good understanding of what you are doing ...

Scavenging will help you clean up old unused records in DNS. Since “clean up” really means “delete stuff” a good understanding of what you are doing and a healthy respect for “delete stuff” will keep you out of the hot grease. Because deletion is involved there are quite a few safety valves built into scavenging that take a long time to pop. When enabling scavenging patience is required. It will work just fine, but not today!
Note: For purposes of this discussion we are going to concentrate on the most common Windows DNS scenario: Windows Server 2003 DNS servers hosting AD integrated zones.
Scavenging is set in three places on a Windows Server:
- On the individual resource record to be scavenged.
- On a zone to be scavenged.
- At one or more servers performing scavenging.
It must be set in all three places or nothing happens.
Scavenging settings on a Resource Record
To see the scavenging setting on a record hit View | Advanced in the DNS MMC then bring up properties on a record.
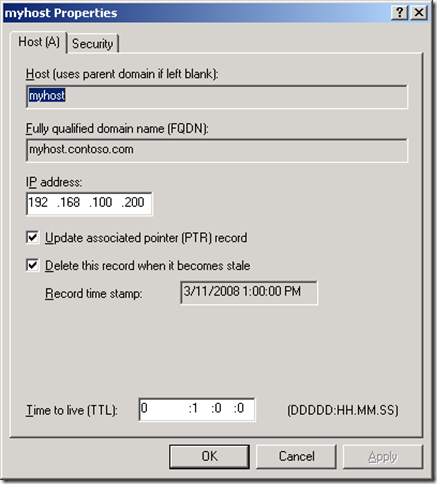 Scavenging gets set on a resource record in one of three ways. The first is by someone coming in here, checking the “Delete this record when it becomes stale” checkbox and hitting apply. When you hit apply the time of day will be rounded down to the nearest hour and applied as the timestamp on the record. Static records have a timestamp of 0 indicating do not scavenge.
Scavenging gets set on a resource record in one of three ways. The first is by someone coming in here, checking the “Delete this record when it becomes stale” checkbox and hitting apply. When you hit apply the time of day will be rounded down to the nearest hour and applied as the timestamp on the record. Static records have a timestamp of 0 indicating do not scavenge.
The second is when a record gets created by a client machine registering using dynamic DNS. Windows clients will attempt to dynamically update DNS every 24 hours. All DDNS records get set to scavenge. When a record is first created by a client that has no existing record it is considered an “Update” and the timestamp is set. If the client has an existing host record and changes the IP of the host record this is also considered an “Update” and the timestamp is set. If the client has an existing host record with the same IP address then this is considered a “Refresh” and the timestamp may or may not get changed depending on zone settings. More on this later.
The third way to set scavenging on records is by using DNScmd.exe with the /ageallrecords switch. Let’s pause here for a few moments to consider a few important words: All, Records, Delete, Stuff. If you actually run this command against a zone it will truly set scavenging and a timestamp on all records in the zone including static records that you never want to be scavenged. Because of the time it takes scavenging to do it’s thing people find this command and get tempted to give it a try. Do not. It will delete stuff. Have patience instead.
Once a timestamp is set on a record it will replicate around to all servers that host the zone. There is one caveat to this. If scavenging is not enabled on the zone that hosts the record then it will never scavenge so the timestamp is essentially irrelevant. The timestamp may get updated on the server where the client dynamically registers but it will not replicate around to the other servers in the zone.
Read the rest of the article @> Microsoft Enterprise Networking Team : Don’t be afraid of DNS Scavenging. Just be patient.





