Microsoft Defender ATP Demo and Walkthrough (Video)
Microsoft Defender Advanced Threat Protection Demo and WalkthroughIn this Tech Talk Andrea Fisher Global Cybersecurity Specialist at Microsoft...
Microsoft Defender Advanced Threat Protection Demo and Walkthrough
In this Tech Talk, Andrea Fisher, Global Cybersecurity Specialist at Microsoft, took us through a great demonstration of new (and upcoming) features in Microsoft Defender ATP (Formerly Windows Defender Advanced Threat Protection) (ATP), as well as many new and upcoming new products including a preview of the new Microsoft Device Manager portal.
How to Access Windows Defender Security Center
Windows defender security center can be found at securitycenter.windows.com. You must have a Microsoft E5 license to use it. Many of the features in this demo and guide are only available if you have the preview features setting enabled in the ATP Advanced Features Settings.
Secure Score
Secure score has come a long way from its humble start as a quick view of your Office 365 security posture, and it keeps showing up in great new places. From the dashboards menu at SecurityCenter.Windows.com you can see your Secure Score for both you Office 365 tenant as well as the score for all of your windows machines. To the right-hand side is a short list of top recommendations that will have the most impact on your environment.
There are over 900 policies monitored including things like BitLocker status, missing security updates, antivirus configuration, and attack surface reduction. Within each improvement, opportunity is suggestions on how to improve that particular issue, and clicking on the number of misconfigured machines takes you right to a list of devices that need your attention. From the machines list, you can export a list to notify responsible teams.
Threat Analytics
Also within the dashboards menu is the threat analytics report. The threat analytics report has articles on new and important vulnerabilities. In addition to an explanation of the attack, below the articles is a list of machines in your environment that have had alerts, and a clickable report on how many machines have had mitigations applied. The list of threats can be sorted by recency or impact.
Custom Security Reports in Power BI
Windows Defender ATP has direct connectors available to Power BI, allowing you to share security information with the rest of your team. To automatically create a new Power BI Dashboard using Windows Defender ATP data, you will click Settings > Power BI > Create Dashboard. From this screen, you can also download the data connector for Power Bi Desktop.
Windows Defender ATP Reporting
Still in preview, Andrea demonstrated the new Reports feature in Windows Defender Security Center. From here you can look for incidents over time, and filter your search based on detection sources, threat category, severity and more. To see it in action skip to the 14-minute mark in the video. Once this feature is publicly available, it can be accessed from the Windows Security Center sidebar menu, or by visiting: securitycenter.windows.com/reports/
Windows Defender ATP Incidents
The new incidents dashboard in Windows Defender Advanced Threat Protection gives you a top-down view of security incidents within your environment, including severity, attack category, numbers of alerts, along with affected machines and users. Incidents are new entities that group together alerts based on automated investigations, file characteristics, time, file or URL. Alerts can also be tagged to manually group them into new or existing incidents.
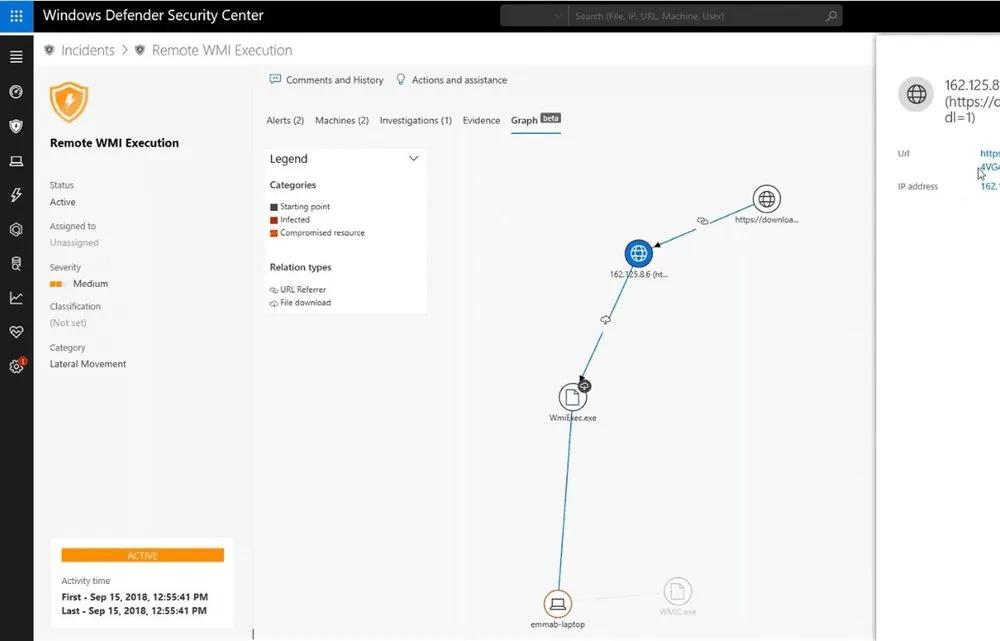
Clicking on an incident gives you a detailed report including recommended actions, the alert process tree and an incident graph report that shows the spread of an incident.
Incidents Graph Tool (In beta)
Available within individual incident reports by clicking the graph tab in the top menu, the new Graph Tool allows you to see a dynamic map that tells the story of a cybersecurity attack. From within the graph, you can see the entry point, affected machines, and how the compromise or activity was detected. Within the map, each node can be clicked on to view details of the malicious file or activity, including both globally observed incidents and the number of incidents, particularly within your organization. When providing post-attack forensics, this new visual tool will be a powerful tool for investigations.
Windows Defender Integrations
There are a host of new integrations available in Windows Defender Advanced Threat Protection security center that can be activated in the advanced settings tab. These integrations allow ATP to communicate with:
- Skype for Business (For one-click communication with users)
- Azure Advanced Threat protection
- Office 365 Threat Intelligence
- Microsoft Cloud App Security
- Azure Information Protection
- Microsoft Intune
Microsoft 365 Device Management Portal
The device management portal is a new portal that collects device management features from other services and provides a singular location for performing device management. This simplified view is more focused and removes the need to jump between Intune, Azure portal and other admin portals. Additionally, this new portal will provide simplified access to the new security baselines feature from Intune, allowing you to create and apply over 300 baselines, monitor device compliance, setting compliance, audit logs, device health, setup mobile threat defense and more. While this is still in preview and not public release, you can access it at: devicemanagement.microsoft.com.
About Agile IT Tech Talks
Agile IT Tech Talks are weekly sessions where we bring in subject matter experts for short, highly focused educational segments, followed by up to an hour of open Q&A where Agile IT clients can discuss their own environments with our engineers and a group of peers. While we release the demos and sessions on our blog, the Q&A benefit is only available to Agile IT Managed Service and Cloud Service Customers. Agile IT is a four-time cloud partner of the year and offers fully managed security as a service. To find out more, schedule a free call with a cloud service advisor.





