What your users need to know about EMS
In the timeless battle between users IT departments companies continue to struggle balancing data security needs with end user productivityThat...
In the timeless battle between users & IT departments, companies continue to struggle balancing data security needs with end user productivity.
That’s why Microsoft developed the Enterprise Mobility Suite, a set of tools that helps companies manage data and devices while enabling users to work from anywhere and any device (yes, even personal ones!)
EMS consists of three pillars that work to unify the user experience:
- Azure AD Premium
- Azure Rights Management
- Microsoft Intune
Each component of EMS plays an essential role in the security puzzle. As more companies leverage the flexibility of the cloud, there are real security concerns to consider. Without proper security protocol and rights management in place, users are essentially free to share out or copy any information or documents that are shared with them. But beyond enforcing the right security measures, you need to know how it affects users and their productivity.
Here’s how each component of EMS impacts your user:
Enabling seamless self-service with Azure AD Premium
Before you can manage documents and devices, you need to know exactly who is trying to access each document. That’s where Azure AD Premium comes into play. As users move on-premises and into the Microsoft cloud, Azure AD Premium creates a unified identity, allowing users to access the growing number of apps they need without having to repeatedly input their credentials and disrupt productivity. Signing on once gives them instant access to thousands of apps. The “My Apps” portal also helps unify the experience for end users. By having these critical business applications in one central location and available within Office 365, users can quickly navigate between platforms and get work done faster.
Because users can access the same mission-critical apps from their phone, they can also be productive even from the road.
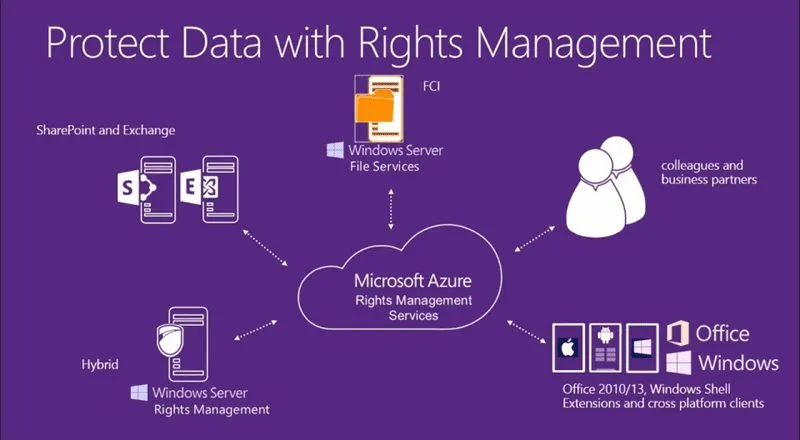
Granting conditional access with Azure Rights Management
The Mobile Device Management aspect of EMS focuses on securing the information rather than the device – allowing users to easily access the data they need from devices while securing protected information from potential threats. For example, if a certain document is encrypted, users do not have the option to copy the information – helping to keep work and personal life separate.
Azure Rights Management also gives you the option to set up one-step or two-step verification. If users forget their password or log in from a new device, they choose whether they want to receive a verification code via text or email. From there, they input the code and quickly regain access to Office 365. This simple step is fast for users but adds another layer of security for admins.
Admins can also lay out the policy without inhibiting user productivity. For example, if users can be productive within the core business apps, they may not need access to personal apps, which admins can control.
Managing mobile devices & applications with Microsoft Intune
When it comes to user productivity, you need to ensure the right information for the right person is displayed on the right device. As the third pillar of EMS, Microsoft Intune allows you to grant conditional access to better manage corporate data. After you’ve set up smart security controls, it’s important to understand what that looks like from the user’s perspective. Upon turning on the verification enrollment processes, users will have to verify their identity using login and password credentials the first time they log in from a particular device. After that, it’s a single sign-on process – meaning users can seamlessly access first and third-party apps from virtually anywhere.
From the company portal, users can see device details and manage apps, remove a device or have it selectively wiped, etc., giving them even more control. Whether users are working in the office or from a mobile device, communicating and working productively across Office 365 is essential. Each layer of EMS works together to deliver a secure yet accessible entryway into critical business apps.
For a complete look at the app management experience from a user’s perspective, check out our webinar here. For more information on how the Enterprise Mobility Suite can benefit your organization, contact Agile IT today for a free consultation!





