Ransomware - See it, Block It, Fix It (Video)
Learn how to tackle shadow IT using EMS and Cloud App Security in Agile IT's video, offering insights into identifying and managing unauthorized IT practices.
Tech Talks are a weekly opportunity to learn how to do more with your cloud software and services. Each week, we feature a short talk from a subject matter expert, followed by a community-driven Q&A where Agile IT customers can ask engineers any of their most pressing questions. This is a free service for our managed service clients. June 28th’s Tech Talk featured a discussion on combating rapid cyberattacks and ransomware by Matt Soseman, a Microsoft Security Architect. Matt has a great blog over at Microsoft that is certainly worth following.
Rapid Cyberattack and Ransomware
The Attacker MindSet
Cybersecurity has changed. Your IP is what nation-states, corporations, and well-funded activist groups want. If your business makes any sort of money, you have something these people want. If you have a secret formula, a patent, or even just a bank account number, you have something these people want. These are talented individuals.
Ransomware and Cyberattack Statistics: [Jump to Video]
82% of successful attacks are coming from:
- Phishing
- Network Scans
- Strategic website compromises
11% are insiders 7% are nation-states 209 hours on average spent hacking one system 140 days is the amount of time a hacker is in a system before they are discovered. Hacker’s concerns:
- Who to target
- What types of attack to launch
- When to launch an attack
- How often to attack
Analysts must react to:
- Who is attacking
- What types of attacks are happening
- When attackers strike
- How often attacks occur
How do We Protect from Rapid Cyberattacks? [Jump to Video]
First, assume we are breached. Next, test and monitor activity in our networks that are performing penetration tests and that are running analytics on our systems.
Ransomware
What is Ransomware? [Jump to Video]
First, ransomware can be delivered from attachments, thumb drives, webpages, and getting hit by a rogue ad on a news site. Then, it installs code on your computer, encrypts all your files, and makes the computer unusable. Thirdly, if files are just stored locally, you’re stuck. Lastly, to get your data back, you must pay a ransom. Without a good backup and recovery process in place, you’re done.
- Increased sophistication (Now we see attackers using AI and cloud technologies to improve the effectiveness of their attacks.)
- Credential Theft
- Lateral Movement Using Exploits – By getting access to admin credentials, they get access to everything.
- Network Scanning and Propagation
- Destructive Behavior (Petya destroyed assets rather than just encrypting)
What are Rapid Cyberattacks? [Jump to Video]
There are three key traits of a rapid cyberattack:
- Fast: Rapid cyberattacks, spread through the enterprise in minutes, leaving very little time to react leaving defenders are completely reliant on prevention and recovery.
- Automated: These attacks are automated with NO human interaction needed. The malware moves from machine to machine using automated sets of traversal techniques.
- Disruptive: Intentional operational disruption via destruction and encryption of systems
Ransomware Defense Strategies [Jump To Video]
Four Key Strategies
- Exploit Mitigation – One of the best things we can do is to make sure we are on current versions of all software we are using. Start with making sure client workstations’ operating systems are fully updated. Move on to servers, routers and even IoT devices (ANYTHING on your network with software).
- Business Continuity / Disaster Recovery – Make sure data is backed up, and the backups are tested.
- Preventing Lateral Travel / Securing Privileged Access – If you get hit with ransomware, it is going to try to find other vulnerable or valuable targets. Segment your access credentials with a focus on reducing the ability or malware to move around the network
- Attack Surface Reduction – Take a look at what software is being run, and do a risk vs. reward assessment. Look at each piece of software and ask yourself if you need it. Every piece of software is more code running on the machine that needs to be patched and defended.
Microsoft Key Recommendations: [Jump to Video]
0-30 Days (Quick Wins):
- Create destruction resistant backups of critical systems and data
- Immediately deploy critical security updates of OS, Browser, and Email
- Isolate computers that cannot be patched
- Implement advanced email and browser protections
- Enable host anti-malware and network defenses
- Implement unique local admin passwords on all machines
- Separate and protect privileged accounts
Less than 90 days:
- Validate backups
- Discover and reduce broad permissions on file repositories
- Rapidly deploy ALL critical security updates
- Disable unneeded legacy protocols
- Stay current, run only current versions of OS and applications.
Using Security Baselines [Jump to Video]
Many of the above recommendations can be configured by automatic security baselines.
- Baselines speed up deployments if you use recommended baselines for Windows 10 and Server 2016
- Consider deploying settings to existing computers via the staged pilot.
- You can download Microsoft’s baselines at aka.ms/security baselines
How Microsoft Can Help Defend Against Rapid Cyberattacks and Ransomware
Microsoft’s expansiveness gives them industry-leading capabilities to providing the tools and guidance needed to secure your systems.
- Visibility - Microsoft has the largest anti-virus and anti-malware service in the world
- Context - Trillions of web pages indexed, hundreds of billions of authentications and monthly emails analyzed, Hundred of millions of reputation lookups, millions of daily suspicious file detonations.
- Experience - 1 million machines protected by enterprise IT security
- Expertise - Established Security Development Lifecycle ISO/IEC 27034-1, works with law enforcement to combat cybercrime and disrupt malware
Microsoft Intelligent Security Graph [Jump to Video]
With Bing scanning 18 billion webpages monthly, Microsoft knows where the malware is and can block it before you find it. With over 450 billion monthly authentications, they have learned the behaviors of bad actors and can identify stolen credentials and alert you. In conclusion, Microsoft scans the dark web for stolen accounts and can alert you so you can disable the account.
Microsoft End to End Protection [Jump to Video]
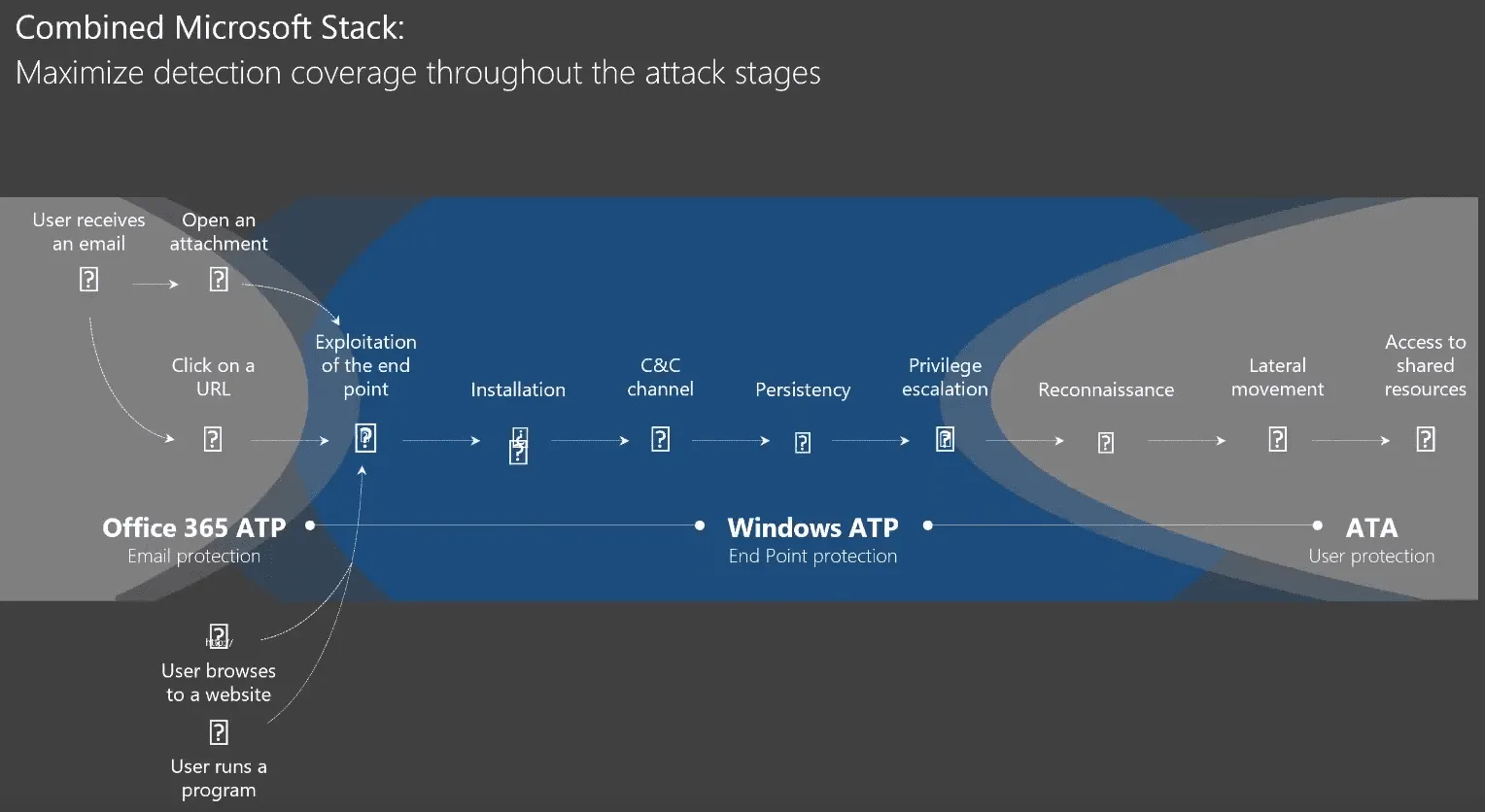
- Online Safety and Protection (Email Protection through Office 365 and ATP)
- Endpoint and server protection (Windows Defender and Windows Server Protection)
- Identity Protection (Azure AD)
- Detect, Investigate & Control (Office 365 Threat Intelligence, Cloud App Security, Secure Score)
- Business Continuity / Disaster Recovery (Azure Backup, OneDrive)
Office 365 Advanced Threat Protection
- Every link and every attachment is scanned and ran on multiple Virtual Machines to identify malware
- Phishing links are identified and blocked. (ATP also has a Phishing Attack Simulator to test your user’s awareness)
Endpoint Server Protection with Windows Defender Suite
- Device guard stops malicious software from being downloaded or spread from other vulnerable systems
- Secure Boot stops MBR attacks
- Windows 10 Kernel Hardening stops attacks using unused or old protocols, such as SMB
- Credential Guard Prevents lateral movement by avoiding credential theft
- Controlled Folder Access makes crypto-attacks impossible
- Windows Defender Advanced Threat Protection gives threat visibility across the entire enterprise to find and stop malware or exploits and uses machine learning to identify suspicious behaviors
Securing Privileged Access Roadmap [Jump to Video]
The Privileged AccessSecuring Roadmap can be viewed at aka.ms/privacy and is designed to raise the cost and difficulty for adversaries attacking privileged access on on-premise and cloud assets. Provides defenses against:
- Credential Theft and Abuse
- DC Host Attacks
- Active Directory Attacks
- Attacker Stealth
Multifactor Authentication
Using Multifactor Authentication is an important way to defend against attacks based on credential theft. User login verification is required for credentials that are stolen.
Azure AD Identity Protection
Enforce risk-based policies using machine learning to identify suspicious behavior, brute force attacks, leaked credentials, and infected devices
Cloud App Security [Jump to Video]
Set up alerts and rules to automatically notify or stop Ransomware behaviors. (For more on Cloud App Security, see Kevin’s talk on Combating Shadow IT)
Advanced Threat Analytics
Detect suspicious behavior based on the user’s normal behavior, such as files and systems accessed, location, time of access and data usage.
Azure Backup
Above all, backing up data is the most important way to avoid impacts from ransomware and cyberattacks. Azure backup can manage full-enterprise backups from a centralized system with no infrastructure.
Combined Microsoft Stack [Jump to Video]
Questions
The Q&A part of the tech talk session allows everyone to ask questions to get in-depth insights applied to their business use-cases. These answers are only available to Agile IT clients and are anonymous to ensure their security and privacy.
- Does Office 365 Advanced Threat Protection work if the user is on Outlook on the Desktop?
- By default, is Office 365 Advanced Threat Protection enabled?
- What is the feature in AD that stops your users from using bad or compromised passwords?
- How does SSO effect lateral traversal attacks?
- If you are not letting the browser remember credentials, can credentials still be stolen?
- How can you clean out all remembered credentials?
- How can you clean out saved credentials across the entire organization?
To find out more about configurations and managed security services, feel free to book a 30-minute consultation with one of our Cloud Service Advisors.





