6 Steps to Delegate Office 365 Mailbox Access Permissions
When managing an Office 365 or hybrid Exchange environment youll likely need to delegate Office 365 mailbox access to additional users at some point...

When managing an Office 365 or hybrid Exchange environment, you’ll likely need to delegate Office 365 mailbox access to additional users at some point.
In certain situations, you could simply create an Office 365 shared mailbox to grant multiple users mailbox access. Many companies take this approach when setting up generic email addresses for the business or specific departments.
But other scenarios are not so straightforward. For instance, if an executive hires an assistant to manage his or her mailbox, the newcomer should not have full access to the Office 365 or hybrid Exchange account. Instead, you’ll want to configure access permissions to give that person limited access and functionality.
A number of other business scenarios will require you to delegate Office 365 mailbox access permissions. So what’s the easiest (and safest) way to set up these permissions?
Enable Office 365 Mailbox Sharing
The process of sharing a mailbox is known as delegating access permissions in Exchange. Whether you’re working in Office 365 or a hybrid Exchange environment, use these steps to delegate Office 365 mailbox permissions:
-
Sign in to Office 365 Admin Center.
-
Select Users > Active Users.
-
Select the user that requires delegate access.
-
Expand “Mail Settings.”

-
Find “Mailbox Permissions” and select Edit.

-
Add or modify users as required. Once complete, select Save.
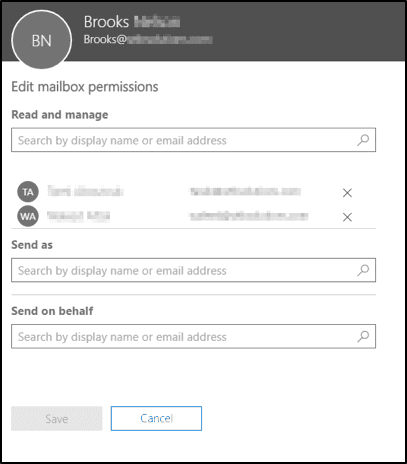
Equipping users with shared mailbox access is one way to extend the ability to read and manage emails, send-as and send-on-behalf.
The steps above are primarily geared towards tier 2 system administrators using the GUI to make changes to your account. You can script all the steps in PowerShell to make bulk changes.
Looking for more help automating or managing your Office 365 infrastructure?
Check out the resources below or reach out today to learn more about our Exchange consulting: Creating an Office 365 Mailbox in a Hybrid Configuration Deleting & Disabling Mailboxes in Exchange Hybrid 2013 & 2016





