Creating disclaimers in all outbound email automatically
The binding terms of disclaimers and their effectiveness is always highly debated but the fact remains that some compliance measures demand ...

The binding terms of disclaimers and their effectiveness is always highly debated, but the fact remains that some compliance measures demand them. Creating a way to have them automatically added to messages when your users email someone outside of the company is a simple and quick setup and doesn’t require any paid or free 3rd party tools.
Any time we want to manipulate or modify a message in transit the one stop shop is mail flow rules, more commonly known as hub transport rules.
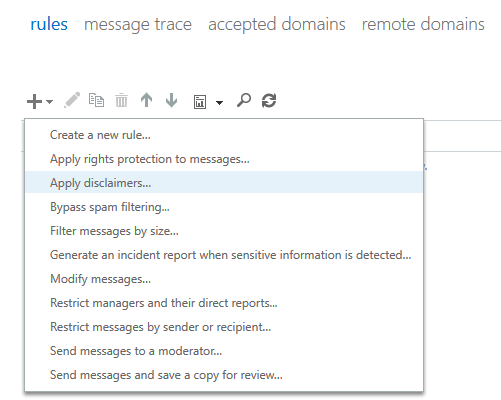
From here it’s just a matter of selecting the types of messages you want your disclaimer applied to. Most commonly the disclaimer will be on all messages with a recipient that is outside of your company. There may be requirements to apply a different disclaimer or only apply the disclaimer if the subject contains a keyword or the sender is located in a specific department in your company.
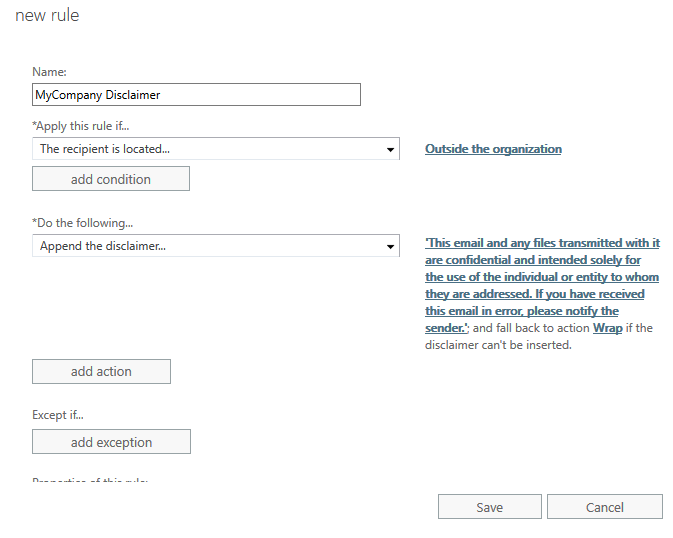
In addition to text; HTML (to include images) and inline CSS can be added to the disclaimer to draw attention by changing the font, text size, or color. With this in mind and the ability to add AD Attribute as well to the disclaimer it’s not uncommon to see companies use the disclaimer to add automatic signatures to emails from their employees. Keep in mind that the disclaimer has a 5,000-character limit to include HTML tags and AD Attribute properties. An example of a signature disclaimer would be:
%%displayname%%
%%title%%
%%company%%
%%street%%
%%city%%, %%state%% %%zipcode%%
Jeremy Sheehan is a Cloud Specialist here at Agile IT, and leads our cloud migration projects for our customers. Jeremy has been working in IT for over a decade, and brings a passion for new technology and a dedication to customer service that we are thrilled to have on our team. To hear more tips and tricks from our technical team, check out our blog. Have questions? Contact us today!





