Explore Mobile Device Management Features in Office 365
Earlier this year we started the rollout of builtin Mobile Device Management MDM for Office 365httpsblogsofficecom20150330announcingg...

Earlier this year, we started the rollout of built-in Mobile Device Management (MDM) for Office 365, and now that it has been available for a while, we want to give you some tips on how to get the feature up and running in your organization.
It’s easy to get started—there are just a few steps, which are documented in detail here: Overview built-in Mobile Device Management (MDM) for Office 365.
• Set up MDM for Office 365—Activate the feature and configure the environment.
• Configure MDM policies—Configure Security Groups and Device policies.
• Enroll devices—When users access Exchange, SharePoint or OneDrive using the MDM-enabled applications, they are required to enroll their devices.
• Manage devices—You can wipe enrolled devices and run reports.
Set up MDM for Office 365
None of your users will be affected by setting up MDM until you configure the MDM policies. So to get started, go to the Office 365 Admin Center, and from the Mobile Devices tab, click Get started.
Depending on the size of your Office 365 tenant, it may only take a few minutes, or it could take a few hours, to activate the feature. In the background, we configure Azure Active Directory and Intune for your users and devices. This is all transparent to you—since you’ll be managing everything from Office 365. You don’t need to wait at this page for the process to complete. Come back when you are ready, and once the feature is activated, you’ll be able to continue the configuration.
You only need to configure a few tenant-wide settings, and you can access them from the Manage Settings link. Set up an Apple Push Notification Service certificate to manage iOS devices and configure any custom domains to support MDM for Windows devices.
How MDM Conditional Access works
MDM policies are applied to groups of users (it will affect all of the user’s devices) and they can enforce Conditional Access to Exchange Online, SharePoint Online and OneDrive for Business through any of the supported mobile applications.
Conditional Access works like this: when a user logs into Office 365 through a supported mobile app, the app checks with Azure Active Directory to see if the user is subject to a Conditional Access policy. If the user has a policy assigned, and the device is not marked as enrolled and compliant, the application prompts the user to enroll the device in MDM. In the case of an Exchange ActiveSync (EAS) client, Exchange sends an email with a link to enroll. Once the user has enrolled the device, the device settings policies are sent to the device, and the user must update the device to meet the appropriate settings such as PIN and encryption. After the settings are updated, the agent on the device informs the management service, which in turn marks the user’s device as enrolled and compliant in Azure Active Directory.
Configure MDM policies
You will want to start by setting up your first policy for a test group of users—you could start with just yourself in the group or add a few eager friends who want to help with the testing, to evaluate the effect on your environment and understand the device enrollment process.
The MDM policies can only be applied to security groups (not distribution groups), so set up a security group (through Office 365 or Exchange) for your test group of users (or use one you already have). To create an MDM policy, select the Manage device security policies and access rules link, which takes you to the Compliance Center, where all the policies for your Office 365 tenant are managed.
The list of policy settings on the first page (What requirements do you want to have on devices?) lists the requirements that need to be met before the user’s device is considered to be compliant. 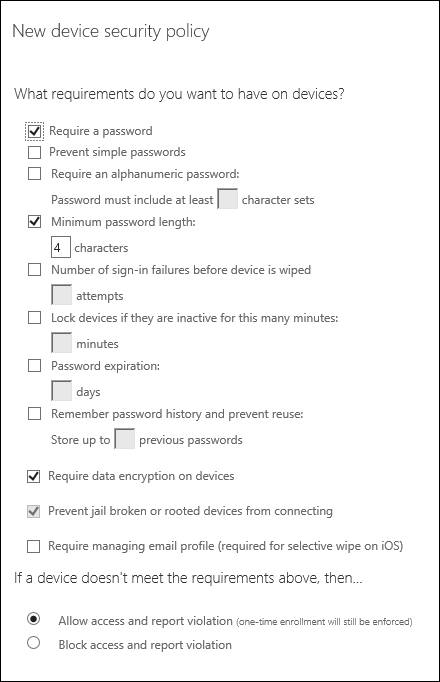
A couple of important notes on a few of the settings:
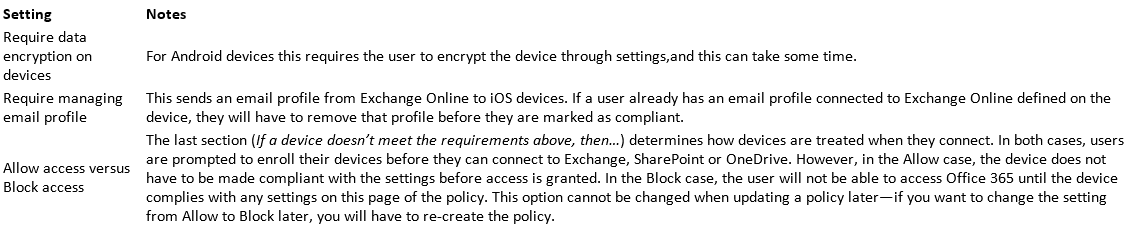
The second page (What else do you want to configure?) has a list of device settings. These settings are pushed down to the device but are not used when calculating whether a device is compliant, and will not stop a device from connecting to Office 365.
The final step is to apply the policy to your group of test users. When you apply a policy to a security group, you need to search for the name of the group (Hint: * will display all groups, or search for the first few letters of the group name).
Once you have created the policy, the status of the policy is “Turning on….” while it distributes the policy to the right systems and changes to “On” once it has completed the policy distribution.
Enroll devices
MDM policies can be triggered when any of the supported Office applications are used on iOS or Android devices. Make sure you have the latest version of the application. When you sign in with your Office 365 credentials (you must be in a Security group that has a policy applied), you will see this enrollment prompt:
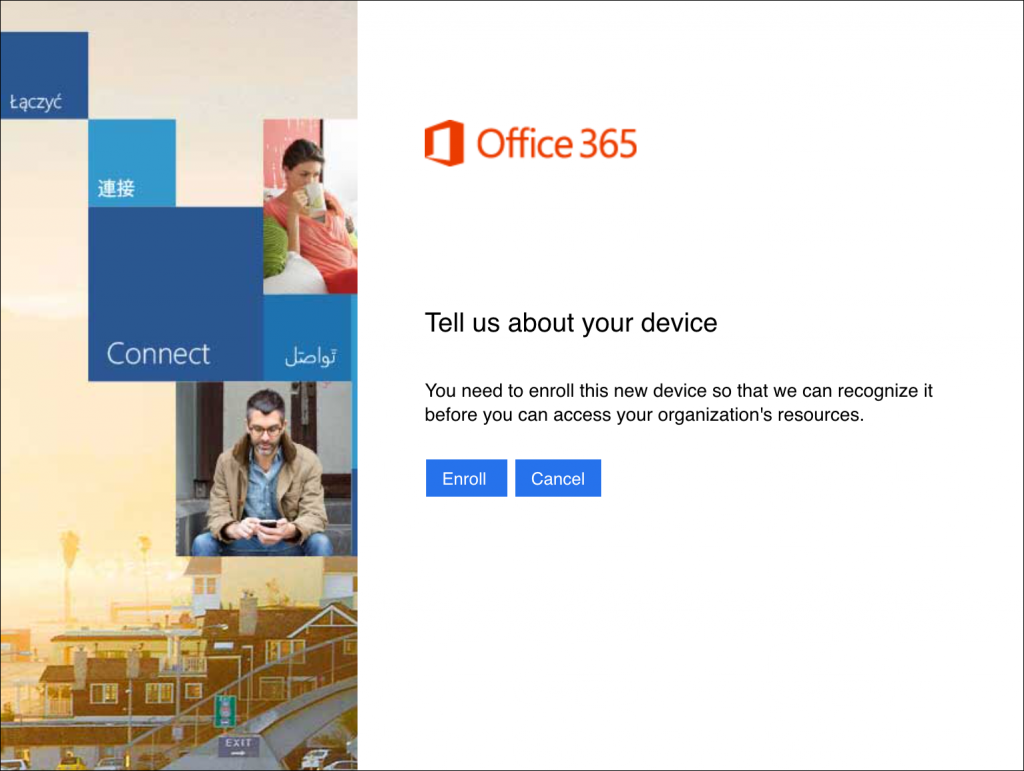
When you tap the Enroll button, you are prompted to download the Intune Company Portal application. Log in to the application and enroll your device. Once all of the required steps are completed, the MDM device settings are sent to the device, and for any settings that haven’t already been configured, you are prompted to configure them.
Simply open the Company Portal app and select Check Compliance to determine if all the settings have been configured correctly. If not, the Company Portal provides a link with remediation steps.


Once the device is compliant, you restart the Office application and connect to Office 365.
MDM policies can also be triggered by using any native email client, which connects using EAS from iOS, Android or Windows Phone 8.1. When you connect to Exchange Online, you receive a message similar to this:
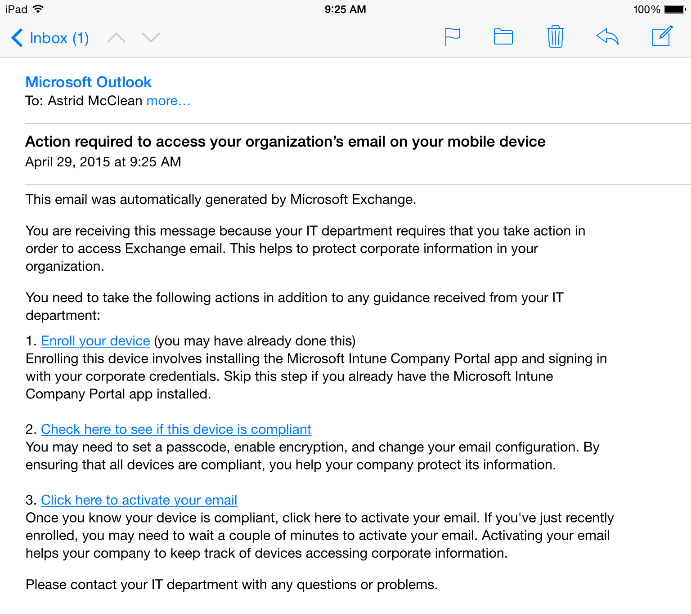
Select the Enroll your device link to go through the same enrollment process (assuming you are not already enrolled) as the Enroll button displayed from the Office applications. Once your device is enrolled and compliant (you can use the second link in the email to check), you also need to click the activate your email link to send the EASid to Active Directory.
For Windows Phone 8.1, there’s no Company Portal to install. Just follow the instructions to add a workplace account. 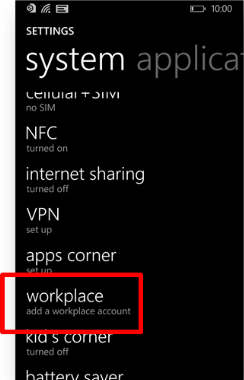
If you have previously connected to Exchange on this same device, then it may take up to 24 hours before your Quarantine mail is received—this is a result of the Exchange service caching your previous compliance status, which was most likely “no policy applies” since this is the first time you have any MDM policies defined.
Manage devices
The Mobile devices page in Office 365 lists all the devices that have enrolled into the MDM service for your tenant. From this list you see details of the devices, as well as issue wipe commands. Office 365 gives you two different wipe options:
• Full wipe—Restores the device to its factory settings, deleting all data on a user’s mobile device.
• Selective wipe—Removes only organization data and leaves installed applications, photos and personal information on a user’s mobile device.
For MDM for Office 365, the selective wipe option will remove the following organizational data:
• Outlook for iOS and Android • OneDrive for iOS and Android • EAS mail for iOS (if the policy option Require managing email profile was defined)
For the other applications that access Office 365 data, and specifically for EAS mail on other devices (or on iOS when the manage email profile policy option was not selected), new access is blocked until the device is re-enrolled, however, existing data is not removed.
From the Office 365 Admin Center, you can also see device compliance reports to display information about the number of devices in your organization that have connected to your environment.
Next steps
Once you’ve tried out MDM for Office 365 with a policy for you and your closest friends, you can educate your users, create additional policies for them (perhaps you need different settings for different groups), and sleep just a little more soundly now that your Office 365 data is better protected.
Want more? MDM for Office 365 has a subset of the features of Intune (see the differences here). So if you are looking for protection beyond what’s included in Office 365, you can subscribe to Microsoft Intune, part of the Microsoft Enterprise Mobility Suite, and receive additional device and application management capabilities for phones, tablets and PCs. This includes the ability to restrict actions such as cut, copy, paste and save as to applications managed by Intune—helping keep corporate information even more secure.
If you want to use both Intune and MDM for Office 365 within the same Office 365 tenant, we don’t support that for all tenants just yet—but you can contact the support team, and we may be able to get you set up as part of our private preview program.
By the way, I talked about using Office 365 MDM at the Ignite Conference in May, so if want to see the product in action, watch the video from the conference.
Try out MDM for Office 365 and let us know what you think! —Astrid McClean, senior program manager for the Office 365 Information Protection team.
The post Explore the built-in Mobile Device Management (MDM) feature for Office 365 appeared first on Office Blogs.





