A closer look at Microsoft EMS from the admin's perspective
The cloud has paved the way to a more productive and collaborative work environment But in breaking down barriers to data sharing security has becom...
The cloud has paved the way to a more productive and collaborative work environment. But in breaking down barriers to data sharing, security has become a top concern for all organizations venturing into the cloud.
The Enterprise Mobility Suite is Microsoft’s solution to this growing apprehension toward data security in the cloud. EMS is composed of Azure AD Premium, Microsoft Intune & Azure Rights Management — a collection of technologies that create a unified identity and experience for both end users and admins.
Microsoft EMS: A Comprehensive Office 365 Security Solution
Together, the components of EMS consolidate user identities so you don’t have to manage multiple identities when people access third-party apps and disable or enable rights as a corporate environment. You also gain the ability to push out and containerize apps onto all types of devices — including iPhones, Androids or Microsoft phones — to better control and oversee user activity.
Ultimately, Microsoft EMS allows admins to work more efficiently when securing their organization and provides peace of mind knowing exactly who has access to which documents and apps, on which devices and from where.
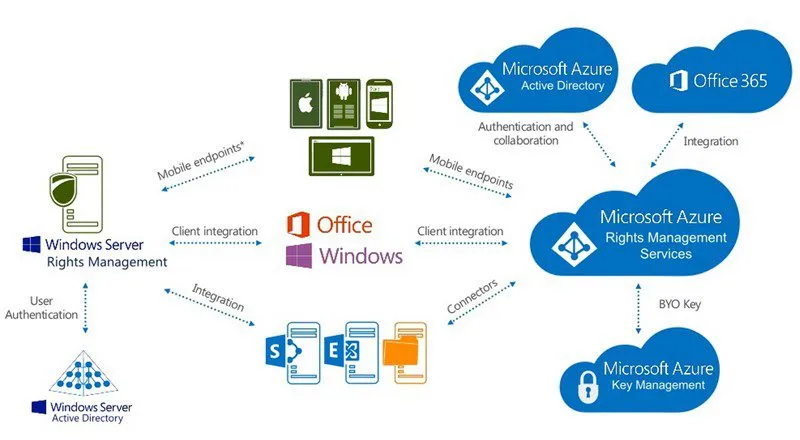
With EMS, Azure is the underlying technology for directory services. You can get to the Microsoft Azure interface via Office 365 or the Admin Center along with the premium features, including single sign-on to 2,400+ apps, multi-factor authentication on-premises or in the cloud, rights management and much more.
Here’s a closer look at each component of the EMS Admin Portal:
Azure Active Directory
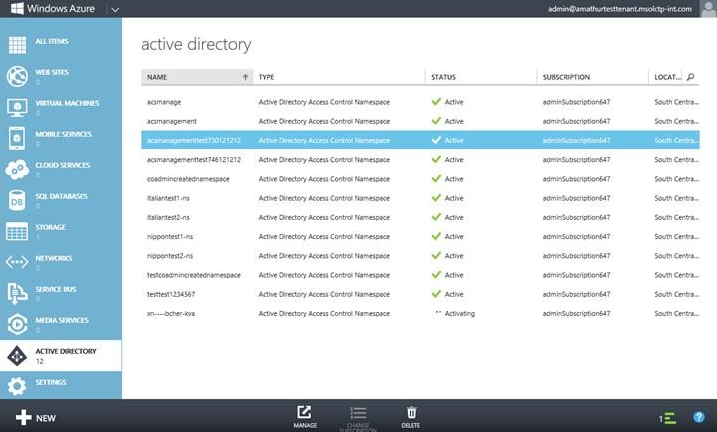 In the Azure AD premium side of the EMS portal, you have complete directory integration and can manage specific aspects of a particular domain, customize your company branding, configure authentication methods, see reports and more. The dashboard clearly outlines anomaly sign ons (e.g., users who have opened apps or logged in from two different cities in one day) and other user reports.
In the Azure AD premium side of the EMS portal, you have complete directory integration and can manage specific aspects of a particular domain, customize your company branding, configure authentication methods, see reports and more. The dashboard clearly outlines anomaly sign ons (e.g., users who have opened apps or logged in from two different cities in one day) and other user reports.
When looking at user identities in the Azure AD portal, you can remove or modify different identities or cloud-based security groups and drill into members and owners of each. For example, you may have a dynamic membership group for salespeople who need to access Salesforce or sales another app. Through Azure, you can easily locate this group and assign the correct app privileges or configure different aspects of Azure AD Premium, such as SSO.
Microsoft Intune
From the Microsoft Azure AD homepage, you can access Microsoft Intune. This single pane of glass gives you an overview of mobile devices, PCs, etc., from anywhere: 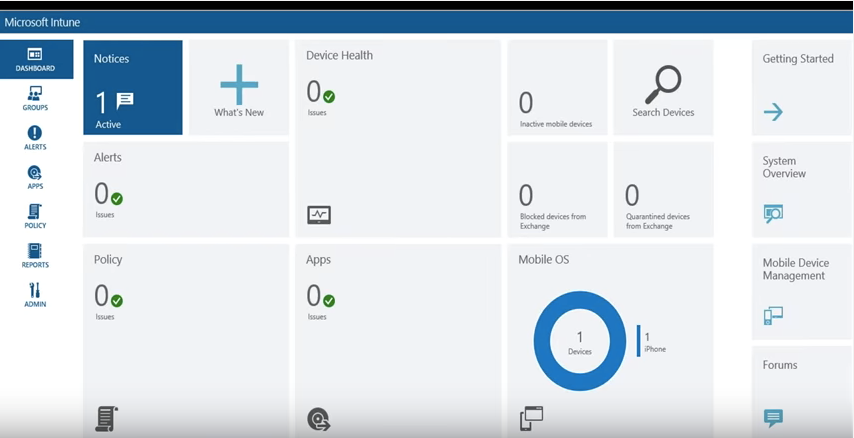
As you can see, the Intune dashboard offers a breakdown of everything going on via green check marks for you to drill down and assess the status of all mobile devices or get information on specific devices.
Because Microsoft handles the vendor relationships, you don’t have to worry about contacting vendors or setting up a trust for your organization when choosing a new app or functionality. Instead, you can go right into configuring multi-factor authentication, bulk adding users, etc.
Overall, Intune is your one-stop shop for managing devices, deploying apps, enforcing policies, and accessing reports to see what apps are running on, what apps each device has installed on it and more.
Azure Rights Management
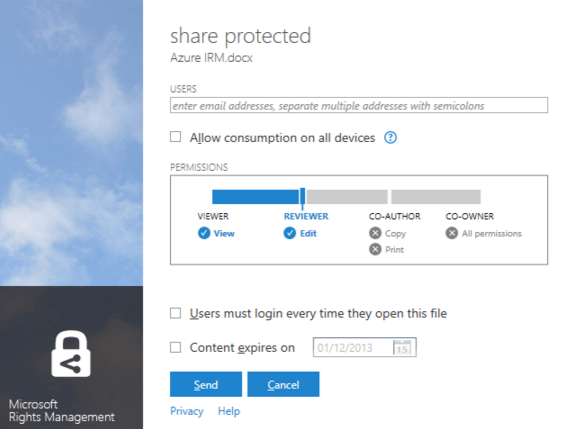 The final component of EMS is Azure Rights Management, which enables you to set up policies. With Azure Rights Management, documents that get sent out to the wild using protective folders can adopt specific rules for individual users. Where users could once cart around these documents after gaining access, now you can manage company data down to the document and user (even on USBs).
The final component of EMS is Azure Rights Management, which enables you to set up policies. With Azure Rights Management, documents that get sent out to the wild using protective folders can adopt specific rules for individual users. Where users could once cart around these documents after gaining access, now you can manage company data down to the document and user (even on USBs).
Within the Azure management experience, you can create policies available or unavailable to users such as taking screen shots of content, copying, sharing data, etc. Microsoft has also made some recent security acquisitions, so new rights management capabilities will soon be available. Enhanced data security features aren’t just nice to have; they’re an absolute necessity in today’s cloud-based world. If you’re unsure whether EMS makes sense for your organization, the AgileEMS POC allows you to trial all the functionalities of EMS to better evaluate its business value.
To learn more about the AgileEMS POC, contact Agile IT today.





